How It Works
Welcome to the new world of Zero Trust.
Our patented Positive Selection® technology is the first of its kind, ensuring Zero Trust data security in every file entering and leaving your systems. Best of all, it happens in real time without ever interrupting your productivity. Now, you can work efficiently, confidently, and safer than ever.
Behind the Scenes of our Patented File Sanitization Process
Votiro’s Positive Selection® Technology
01
Step 1
Unsafe/untrusted file is received with potential privacy and security risks
02
Step 2
File is automatically dissected into content, objects, and templates
03
Step 3
File content is rebuilt on top of known-safe templates – masking sensitive info and removing any potential malware
04
Step 4
100% safe, fully functional, and compliant file is delivered to endpoint and users
Votiro pioneered Zero Trust Content Security. Today, we go beyond existing solutions to provide the very best in threat prevention and data security.
We stop file-borne threats by ensuring every file is examined and sanitized, no matter what.
the rest…
Predictions based on a signature-based list or collaborative database, which leaves room for zero day threats to breach your endpoints.
Virtualization aimed at
predicting outbreaks, but can slow down productivity and still allow some malware to sneak through.
Solution that highlights threats that have reached the endpoint and alerts for after-the-fact mitigation – which is far too late for true protection.
Votiro Solutions
Content is everywhere.
So is our Zero Trust protection.
Privacy & Compliance
Keep sensitive information private and in the right hands.
Email Attachments
Prevent 100% of file-borne attacks delivered via email.
Browser Downloads
Prevent hidden threats in files downloaded from the web.
File Uploads
Stop malware from entering web portals and applications.
Data Lakes
Ensure your data lakes are free from hidden threats.
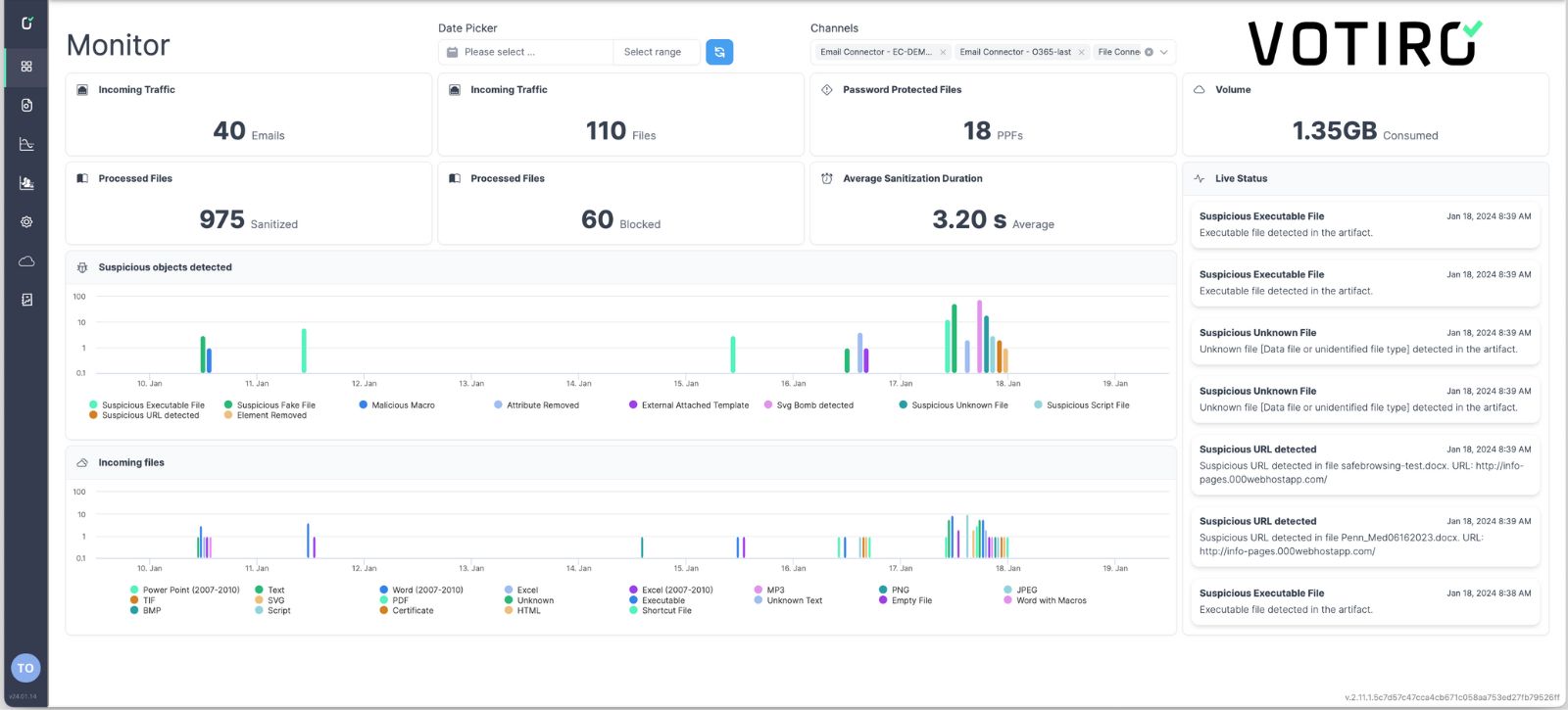
Threat Analytics
Get actionable insights into your files and risk surface.
Collaboration Tools
Protection where work happens most – locally and remote.
Web Apps API
Keep incoming information secure wherever it’s uploaded.
File Transfers
Exchange files in bulk, quickly, efficiently, and without threat.
All Solutions
You’ve only scratched the surface… of your risk surface.
See how Votiro protects your data in real-time.
Schedule a personalized demo to learn how Votiro plugs security gaps in your organization.
Trusted by Leading Industries
Votiro enables customers to digitize and collaborate on files without creating new operational burdens.