From Reactive to Proactive: Using Analytics to Understand and Prevent Cyber Attacks

In recent years, the landscape of cyber threats has dramatically transformed, marked by increasing complexity and frequency. As the digital footprints of organizations expand, so do the variety of attack vectors. Understanding the source, targets, and plan of attack is crucial for efficiently preventing these threats.

Who is at Risk from Cyber Attacks?
High-value targets such as CEOs and engineers are often in the crosshairs, facing sophisticated cyber attacks from seemingly benign sources.
Common sources of attack include:
- File shares
- Software as a Service (SaaS) platforms
- Web applications
Notably, there has been a significant shift in attack methodologies, moving away from traditional channels like email to more integrated platforms used for collaboration, as well as cloud storage services.
Enhanced analytics are crucial for staying ahead of how cybercriminals will attack your organization and taking preventative actions to stop it.
The Ever-Present Threat
Cybercriminals like to use attacks that are low effort, yet still effective. This is why malware and other hidden threats in files remain a persistent challenge for businesses around the globe. Despite the long-standing presence of Antivirus (AV) software in the cybersecurity arsenal, it alone proves insufficient in fully thwarting these threats—a fact that underscores the complexity and sophistication of modern cyber-attacks.
The reason for this gap in defense lies partly in the relentless evolution of these malicious attacks. As cybercriminals continuously refine their techniques and develop more complex forms of malware, traditional AV solutions struggle to keep pace. This evolving threat landscape demands more advanced and dynamic approaches to cybersecurity, highlighting the need for businesses to adopt multi-layered defense strategies that go beyond conventional AV protection to safeguard their digital assets effectively.
The Unknown Malware Dilemma
The dilemma of unknown malware, encompassing zero-day threats, ransomware, and its various strains, presents a formidable challenge for businesses. These insidious forms of malware often elude initial detection by conventional AV software, which relies on signature files to detect known strains. This creates a dangerous window of opportunity for attackers.
While antivirus solutions serve as a crucial starting point in the defense against cyber threats, they primarily intercept and neutralize known dangers. They quickly and efficiently stop these threats but require further investigation by human experts on more ambiguous or novel threats. This scenario burdens cybersecurity teams, who must delve deeper into the analysis to distinguish between benign and malicious activities.
Multi-stage attacks
Cybercriminals rarely do a direct attack and bail. Instead, they take a multi-staged approach called the Cyber Kill Chain.
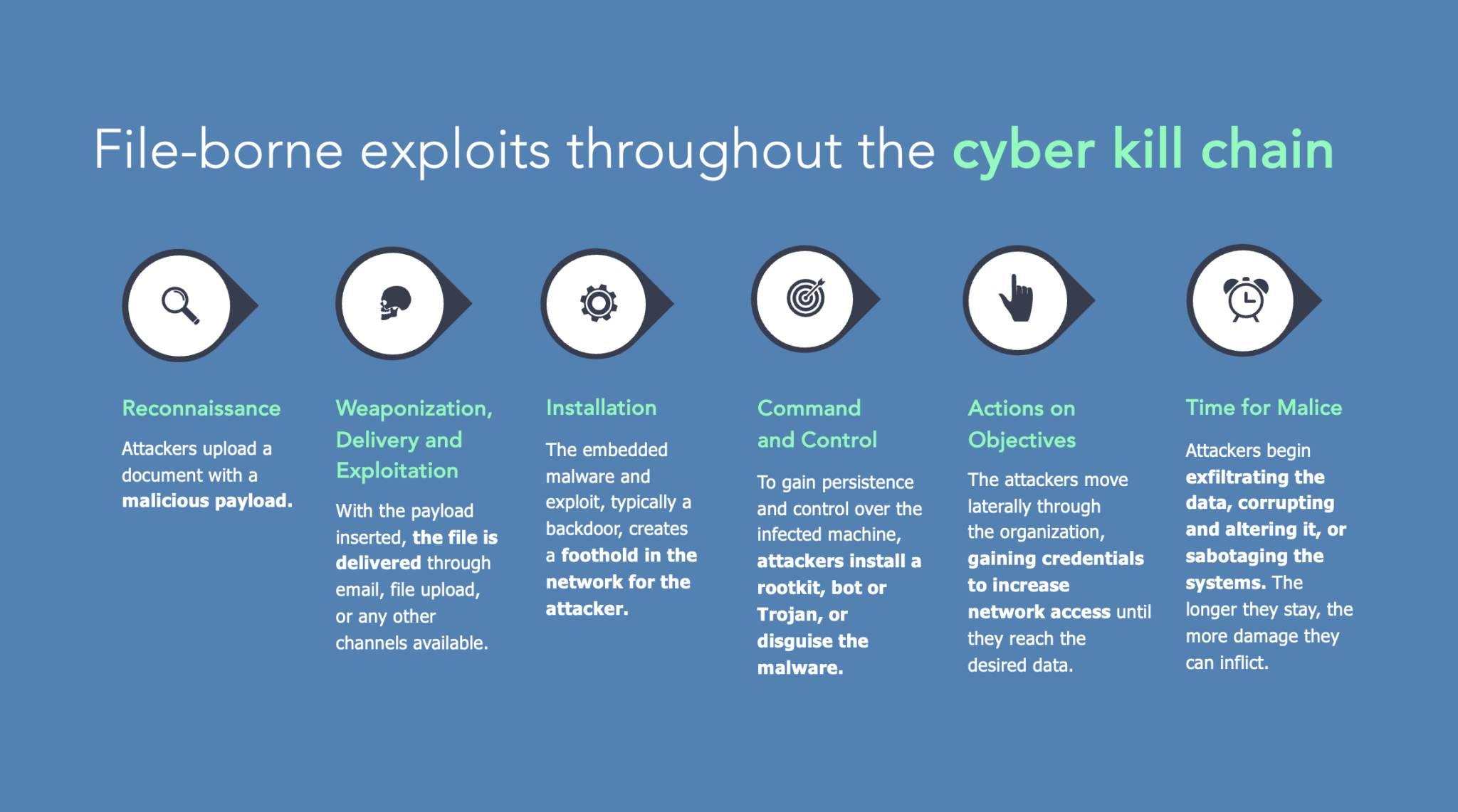
This framework segments a cyber attack into various stages, beginning with reconnaissance, where attackers gather information about their target. Each attack step builds upon the previous one, gradually escalating from initial probing to the final execution of the attack.
One of the critical challenges in countering these attacks is that some stages can appear benign, often slipping under the radar of most security software.
For instance, the reconnaissance phase (aka establishing a foothold within a network) might not trigger traditional security alarms as they don’t exhibit overtly malicious behavior. This subtlety allows attackers to advance undetected, emphasizing the need for more nuanced and adaptive security systems to identify and respond to these early and seemingly harmless stages of a cyber attack. That, or stopping the potential attack well before it can reach an endpoint.
Shifting from Reactive to Preventative Cybersecurity
The paradigm shift from a reactive to a preventative approach in cybersecurity marks a significant evolution in how organizations defend against cyber threats. This shift entails moving away from solely relying on after-the-fact analysis and proactively preventing threats before they materialize.
A crucial element of this proactive stance is incorporating external data sources and threat feeds into comprehensive analytics. These resources are invaluable in identifying and understanding currently active attacks, providing real-time insights into the threat landscape. By analyzing these data streams, organizations can discern patterns and trends in cyber attacks, enabling them to anticipate and prepare for shifts in attack methodologies.
This forward-looking approach empowers organizations to respond to current threats and strategically fortify their defenses against emerging trends and evolving attack vectors, thus staying one step ahead in the constant battle against cybercrime.
Understanding the “Where”
One of the core steps in this process is understanding the where. Organizations today ingest files from myriad sources, each potentially serving as a gateway for unsafe files. These sources range from traditional emails to modern collaboration software like SharePoint, Teams, Slack, cloud services, partner portals, and web applications. Each channel represents a potential entry point for cyber threats, adding to the organization’s attack surface.
The ability to detect these risky entry points in real-time is a critical step in bolstering the security posture. Identifying and addressing these security gaps can rapidly mitigate threats before they escalate. This understanding enables organizations to develop and implement prevention policies that are specifically targeted at the areas most vulnerable to attacks.
Determining the “Who”
Like knowing where the attack stems from, knowing who is involved is crucial to an effective defense strategy. This process involves identifying the perpetrator of the attack and recognizing potential insider threats within the organization. Understanding the identity or characteristics of the attacker provides invaluable insights into the nature and possible objectives of the attack.
Additionally, pinpointing the specific targets of these attacks, such as individuals or departments, is equally crucial. This knowledge is particularly beneficial in defending against targeted threats like spear phishing, where attacks are tailored to specific users or teams. Responses can be more efficient and effective by focusing defenses and alerts on these targeted users rather than issuing broad warnings to the entire company.
Moreover, suppose a particular user is the focus of multiple attack strategies, such as credential theft. This information can be integrated into a Security Information and Event Management (SIEM) system. This integration enhances the SIEM’s capability to detect and prevent threats, thereby fortifying the organization’s overall security posture against sophisticated and targeted cyber attacks.
Determining the “How”
Once you know who and what is being targeted, the next piece of information necessary is understanding how the attackers intend to do it. This process involves identifying the specific mode or method of the attack, which in turn enables organizations to automate preventative remediation strategies. Organizations can tailor their defense mechanisms more precisely by understanding the nature and type of threat – a sophisticated ransomware attack, a phishing scam, or a network breach.
This knowledge also facilitates targeted threat hunting, allowing security teams to focus their efforts on the most likely attack vectors and tactics used by cybercriminals. Recognizing the mode of attack enhances the effectiveness of real-time threat detection systems. These systems, equipped with the latest intelligence on attack methodologies, are better positioned to identify and neutralize threats proactively. The advantage of such proactive remediation is immense, as it addresses threats as they occur and helps preempt potential future attacks.

Votiro Delivers Advanced Analytics
Votiro revolutionizes cybersecurity through its in-depth threat analytics dashboard, providing organizations with a real-time method to combat cyber threats. This dynamic dashboard accelerates the examination of genuine threats and determines the where, who, and how behind file-based attacks, helping your organization focus on prevention.
To build a truly comprehensive defense, Votiro helps organizations build beyond conventional security measures such as Endpoint Detection and Response (EDR), AV, and sandboxing alone.
Votiro bridges the gaps left behind by traditional security methods, offering detailed and actionable insights into the subtleties of suspicious file content. Its capabilities extend to accurate file typing, in-depth macro analysis, monitoring external actions, and beyond. As a blend of premier antivirus defense and a comprehensive analytics platform, Votiro provides a twofold advantage: safeguarding against known threats while equipping users with powerful tools for comprehending and tackling potential security vulnerabilities.
Contact us today to learn more about how Votiro delivers proactive cybersecurity and provides the visibility your organization needs to efficiently stop hidden threats in files – today and in the future.
News you can use
Stay up-to-date on the latest industry news and get all the insights you need to navigate the cybersecurity world like a pro. It's as easy as using that form to the right. No catch. Just click, fill, subscribe, and sit back as the information comes to you.
Sign-up Here!
Subscribe to our newsletter for real-time insights about the cybersecurity industry.