How the 2019 LinkedIn Phishing Campaign Caused a Cyber Disaster
Job security has taken on a new meaning, with a new cyber-espionage attempt that has recently come to light. Between September to December 2019, employees at select aerospace and military organizations in Europe and the Middle East were targeted with a LinkedIn phishing campaign. The campaign’s malevolent goal was to gain intelligence information about employees and, in some cases, to monetize the attack by compromising their business emails.
The attack methods and financial angle have led Internet Security company ESET to suspect that the attack originated from the Lazarus Group, a notorious North Korean hacking group used to fund the country’s illegal weapon and missile programs. The campaign was cleverly executed via a series of phases:
Phase 1: Initial contact and compromise
The attackers created several fake LinkedIn phishing accounts, each impersonating HR managers from major US companies operating in the aerospace and defense market, including Collins Aerospace and General Dynamics. The hackers used LinkedIn’s messaging feature to dangle fake job offers to targeted employees in specific companies in the hopes of engaging them. The attackers chatted with the victims, building enough of a relationship to convince them to open malicious files. Here is an example of a LinkedIn phishing communication between the hackers and the targeted employees.
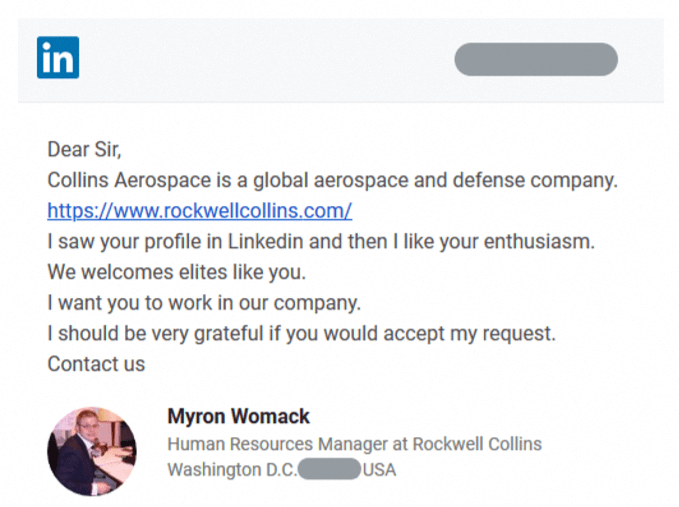
Once they succeeded in engaging their prey, the attackers included malicious RAR archive files within the communication, disguising them as documents related to the advertised job offer, such as a PDF document detailing salary information of specific job positions.
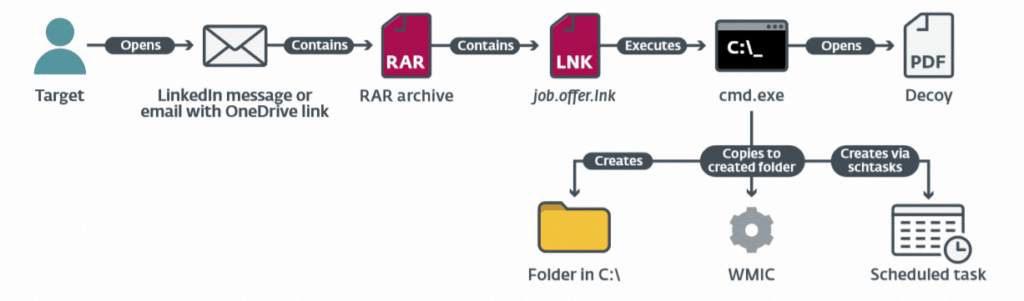
In actuality, when the unsuspecting target opened the malicious file from the LinkedIn phishing campaign, it executed Windows’ Command Prompt utility to perform a series of actions, injecting malware into the computer and successfully compromising the network. Here is the attack scenario from initial contact to compromise:
Phase 2: Intelligence gathering
Once they accessed the network, the attackers explored the environment using PowerShell commands, as well as other custom malware tools. One malware sample named Inception.dll, served to inspire ESET to name the campaign Operation In(ter)caption. The hackers’ reconnaissance paid off: they managed to obtain the list of company employees including administrator accounts. They then performed password brute-force attacks on these accounts.
The hackers managed to stay under the radar by abusing preinstalled Windows utilities to download, decode, and execute their tools in an effort to hide malicious activity among legitimate processes. They also covered their trails: when they finished their covert activities, the attackers removed all the malicious files from the compromised computer. It is also worth noting the sophistication of these attacks: the hackers utilized both legitimate servers as well as their own, using Windows operating systems and Microsoft’s IIS as a web server.
Phase 3: Business Email Compromise
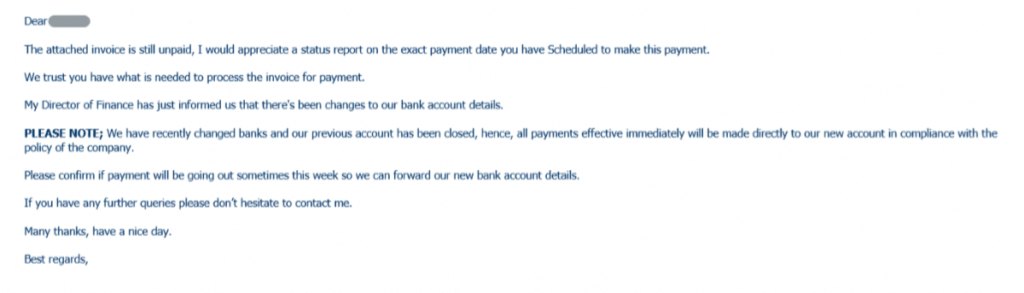
While the main goal of the LinkedIn phishing scam was to steal company data, the attackers also tried to take advantage of their newfound access to the victim’s email account to gain financially. In one example, the hackers found an ongoing email communication between the targeted employee and a customer about an unresolved invoice. The attacker hacked into this conversation using a similar-but-bogus email address and encouraged the customer to transfer the balance into an alternate account number. Their plan was foiled when the customer contacted the victim’s correct email address. The victim realized his system had been compromised and reported the incident.
Unfortunately, these types of social engineering attacks are not uncommon. The only way to stop file-borne macro-based threats, including zero-day malware that can’t be detected by traditional protection solutions, is to invest in a solution that neutralizes all malicious elements in any and all incoming files.
Votiro is the only solution that guarantees complete protection from weaponized files. Unlike Secure Email Gateways or detection-based file security solutions that scan for suspicious elements and block some malicious files, Votiro’s revolutionary Positive Selection technology singles out only the safe elements of each file, ensuring every file that enters your organization is 100% safe. Votiro’s innovative approach to file security works invisibly in the background, completely eliminating threats while ensuring zero interruption to business.
To learn all about Votiro, including our Zero Trust CDR and DDR capabilities, you can sign up for a one-on-one demo of the platform. You can also try out the platform free for 30 days and see how we can protect you from the next phishing attempt.
News you can use
Stay up-to-date on the latest industry news and get all the insights you need to navigate the cybersecurity world like a pro. It's as easy as using that form to the right. No catch. Just click, fill, subscribe, and sit back as the information comes to you.
Sign-up Here!
Subscribe to our newsletter for real-time insights about the cybersecurity industry.



