How Our CDR Solutions Disarmed a Malicious Password-Protected File
Attacks by malware are continuously growing, with AV-TEST Institute registering more than 400,000 new malware pieces every day. These malicious files use high-obfuscation algorithms to hide from traditional anti-malware detection solutions, and unfortunately, the threat actors are becoming more and more successful.
One technique that has seen a positive track record for evading detection is when a malicious document is password-protected, and the password is given in the email body, making it easy to trick unsuspecting users into opening the malicious file. Password protection makes it harder for traditional detection solutions to scan the attachment for malicious code.
One example of a recent malware attack that originated in a password-protected file is described below.
Anatomy of a Recent Attack
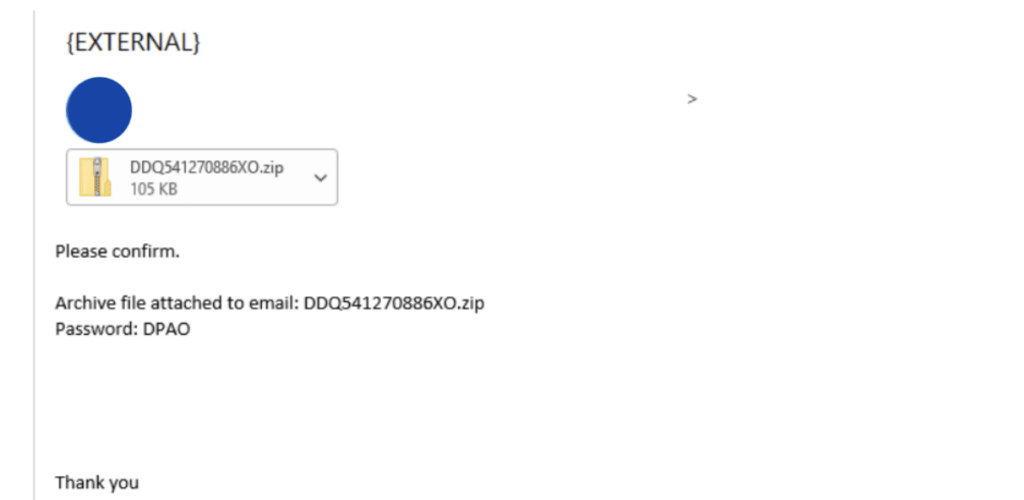
In February 2022, a hacker infiltrated a legitimate healthcare company’s email and sent a malicious password-protected zip file named DDQ541270886XO.zip to a large insurance company.
The ZIP password was included in the body of the mail along with a fake message that read, “Please confirm. Archive file attached to email: DDQ541270886XO.zip. Password: DPAO.”
When an employee at the insurance company received the compromised email with the password-protected file and the required password to access the file, it raised no suspicions.
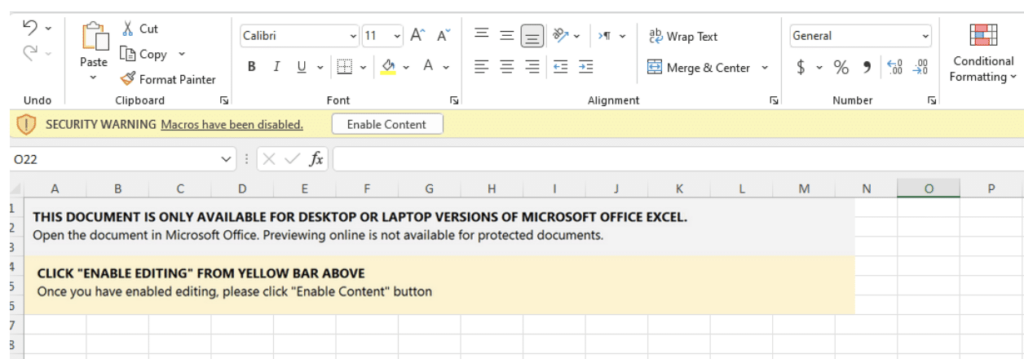
The unsuspecting employee opened the zip file with the provided password and found an innocent-looking Microsoft Excel document inside. The Excel document displayed the classic “Enable content” message, asking the user to enable the malicious macro.
Macros are a legitimate component of Microsoft Office and are used for automating tasks, such as creating documents, spreadsheets, and presentations. Unfortunately, these mini-programs are easily compromised by hackers.
Once the user enables the macro, the threat actor wins, and the malicious code enters the organization. But, lucky for this particular insurance company, their network was protected by Votiro.
How Votiro Removed the Threat from the File
Votiro’s zero trust content disarm and reconstruction technology proactively disarms files of known, unknown, and zero-day malware threats so organizations can rest easy knowing that employees can download, open, or use the files they need for their work without fear of an attack. Votiro’s technology sanitizes all files – regardless of origin – without adding friction, interrupting user or application workflows, or impacting file fidelity.
While a malicious macro attack is challenging to detect, Votiro’s machine learning algorithms identified the threat and sanitized the file before it could wreak havoc on the company’s network. When Votiro detected the file, the hash could not be found on the VirusTotal database –and still cannot be found as of today – meaning the malware is still unknown to the security community.
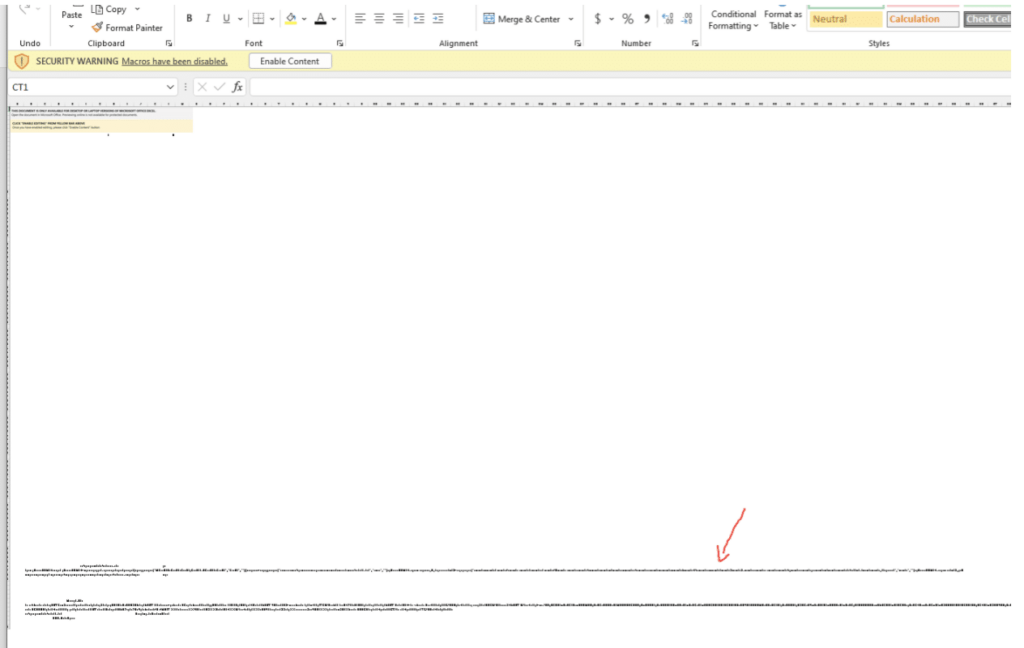
As part of the manual investigation of this particular file, Votiro changed all the content to black text. This caused the malicious code to appear, as the hackers hid some malicious content at the bottom of the Excel file by writing the code in white.
Below is a screenshot from the customer’s user interface, highlighting that the malicious macro was removed and the zip file was sanitized for use.
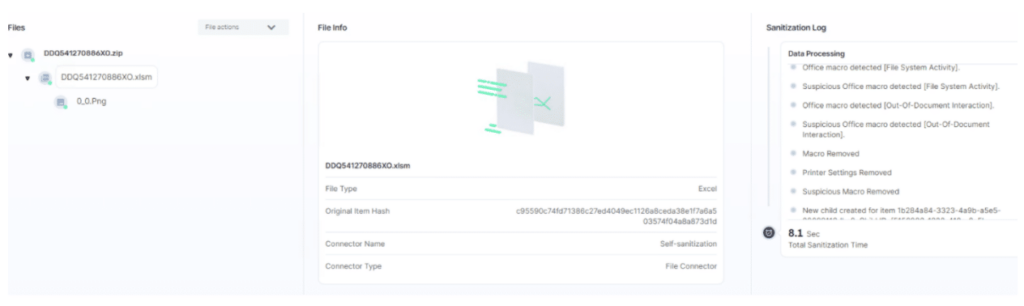
For more information on how Votiro’s patented Positive Selection® technology can help your organization avoid the pitfalls of falling victim to a malware or ransomware attack hidden in incoming content, watch the below 2-minute demo video or contact us today for a customized demo.
News you can use
Stay up-to-date on the latest industry news and get all the insights you need to navigate the cybersecurity world like a pro. It's as easy as using that form to the right. No catch. Just click, fill, subscribe, and sit back as the information comes to you.
Sign-up Here!
Subscribe to our newsletter for real-time insights about the cybersecurity industry.



