Excel-based Hidden Malware: How Old Tech Leads to New Cyber Threats

As one of the most popular software for office productivity, Microsoft Excel is used daily across a broad spectrum of organizations, large and small. Excel 4.0 was released in 1992 and became highly popular for its macro functionality…so popular that this old-school technology is still commonly utilized in many legacy operations. Unfortunately, hackers have realized its importance to many organizations and have found ways to weaponize these files widely used for finances or record keeping. This blog explores how payloads are still being delivered through Excel 4.0 macros – after 30 years – the recent trends to watch for, and how companies can allow their employees to utilize macros without fear of hidden malware.
Malware delivery leveraging Excel macros
Since Microsoft introduced Excel 4.0, hackers have found ways to use Excel sheets and macros to deliver malicious files, upping their methods to stay one step ahead of the security community. Recently, there has been a marked spike in evasive malware payloads delivered through Excel 4.0 macros.
During the second half of 2020, bad actors began concentrating their efforts on the XLSX file format, specifically by entering malicious code directly into workbook cells and by using API level functions to call other processes, such as downloading a file, creating a file, and invoking PowerShell or cmd. As the anti-virus solutions caught on, hackers further fine tuned their methods by shifting to the XLSM file format. 2021 saw a new trend by attackers to use legacy Excel 4.0 XLM macros instead of the more advanced VBA macros to bypass anti-malware systems.
Examples of threats using this method
Zloader: Recently, legacy users of Microsoft Excel were targeted in a phishing campaign that uses an innovative evasive malware technique to disable Office security mechanisms and deliver the Zloader payload without triggering alerts. Zloader is a banking trojan designed to steal credentials and other customer details from financial institutions. When the user opens the XLSM file, a legitimate-looking image prompts the user to enable the content.
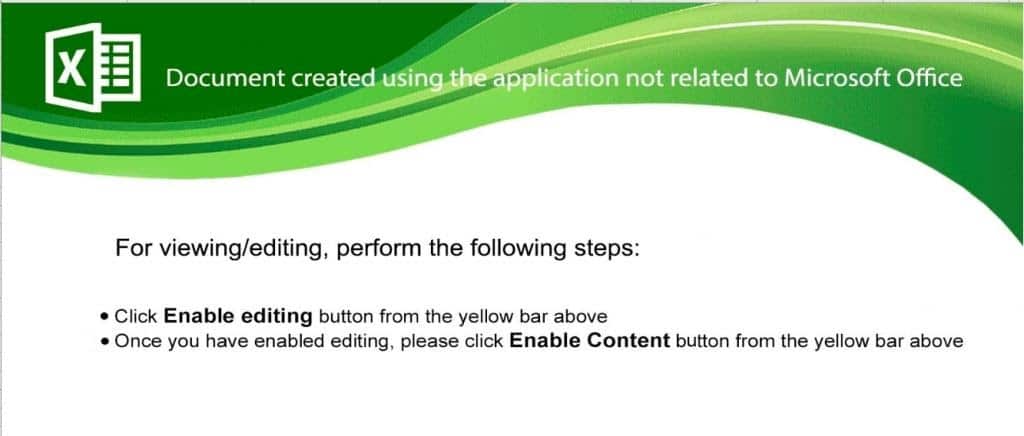
MirrorBlast: A Q4 phishing campaign known as MirrorBlast starts with a document attached to an email. Later, the attack uses a Google feed proxy URL with a SharePoint and OneDrive lure that poses as a file share request. When users click on the URL, they are directed to a compromised SharePoint or OneDrive site, leading to the weaponized Excel document.
Qakbot: A recent campaign utilized Excel 4.0 macros (XLM) to deliver Qakbot malware. Qakbot is a well-known banking Trojan that is currently used as a general loader for other payloads. An email containing a malicious URL is set to an unsuspecting target, which retrieves a zip file with a file name that matches that of the target. This zip archive contains a malicious Excel file (xls) that, when opened, runs an Excel 4.0 macro that downloads and executes a malicious DLL/Qakbot payload.
IcedID: Banking trojan IcedID, also known as BokBot, targets user financial information and acts as a dropper for other evasive malware, including ransomware. Security researchers reported more than 15,000 HTTP requests from malicious Excel files carrying an extension over three months, making this a worrying trend.
How Votiro Combats the XLSM Threat
The only way to stop macro-based threats including zero-day malware that traditional protection solutions can’t detect is to invest in a solution that proactively removes malicious elements in incoming files… without searching for them.
Votiro helps companies deliver safe and functional files to their users and applications, wherever and however files enter. Votiro disarms malicious files – including Microsoft XLSM files – at lightning speed and massive scale without slowing data flow or interrupting business workflows or app-to-app processes. With Votiro, both known and unknown threats hidden in files are eliminated so that no process is stalled and no one has to think twice about downloading, opening, or using the files they need for their work.
To learn more about implementing Votiro’s patented Content Disarm and Reconstruction (CDR) technology to secure your network against malicious XLSM files and other threats, please schedule a demo today.
News you can use
Stay up-to-date on the latest industry news and get all the insights you need to navigate the cybersecurity world like a pro. It's as easy as using that form to the right. No catch. Just click, fill, subscribe, and sit back as the information comes to you.
Sign-up Here!
Subscribe to our newsletter for real-time insights about the cybersecurity industry.



