Anatomy of an Advanced VEC Attack Using a Password-Protected Zip File

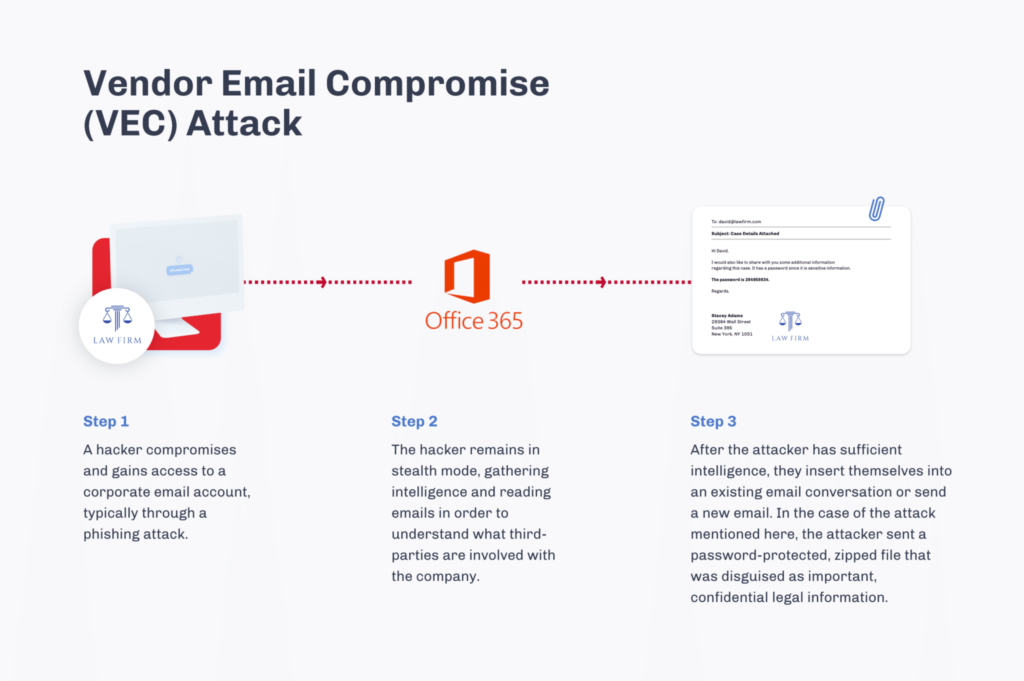
Recently the news has been full of high-profile cyber attacks perpetrated through an email phishing technique called Vendor Email Compromise. A VEC attack is when a hacker hijacks a legitimate email account to send malicious messages to an innocent victim. As the originating email comes from a trusted partner or supplier – and often contains legitimate business and personal details – the malicious messages easily pass domain authentication and other traditional security controls, making this method of attack highly successful.
VEC attacks can be devastating. According to the FBI’s 2020 Internet Crime Report, the federal agency received just under 20 thousand complaints of Email Compromise attacks in 2020, accounting for over $1.8 billion in losses. Cyber-criminals have recognized a golden opportunity: with today’s interconnected business partnerships, a single breach can impact many more organizations along the global supply chain.
One example of a recent, zero-day VEC attack that delivers a Valyrian trojan upon execution – and that Votiro discovered and prevented – is below.
Anatomy of a Recent Vendor Email Compromise Attack
On March 2nd, 2021, a hacker infiltrated the email inbox of a legitimate law firm, and sent a malicious password-protected zipped file to a large insurance company. The insurance company and the law firm had been engaged in back-and-forth communications for some time. Therefore, when the insurance company employee received the email with the password-protected file and instructions to review the legal documents inside, it raised no suspicions.
The malicious email bypassed the insurance company’s existing secure email gateway and other email security solutions’ reputation and validation checks. When Votiro analyzed the email, headers specifying McAfee and Sophos embedded engines were up-to-date.
Based on the existing relationship between the sender and recipient, the insurance company employee typed in the password for the zip file, unlocking the infected files. The employee then opened the files inside of the Zip archive.
Once the files were opened, the virus inside —a Valyrian trojan—would have executed and infected the corporate machine. VB:Trojan.Valyria.3963 is a zero-day Valyrian trojan, named after the indestructible steel from the series Game of Thrones. This malware contains wide-ranging functionality and multiple propaganda methods, with devastating consequences when deployed. This family of malware is also very stealthy: Valyria remains concealed in the victim’s system by writing itself to the Windows startup folder, executing automatically on computer startup.
Why Traditional Email Security Missed this VEC Attack
The timeline from this malware’s point of creation to delivery to the employee inbox was just 2.5 hours, rendering it a zero-day and unknown threat. The insurance company’s existing email security solutions could not detect and prevent zero-days and unknown threats, as they operate based on signature databases of previously existing and known threats.
In addition, the malicious code was obfuscated by being password-protected, encrypted, and zipped, which traditional malware scanners deem “unscannable.” The hacker took advantage of this success and replicated this VEC several times, wreaking havoc across multiple businesses until antivirus software identified the attack and added the code to its databases six days later.
How Votiro Prevented the Threat from Executing
In this particular attack, the attack made it to the victim, but did not execute.
The insurance company had previously deployed Votiro, which proactively cleansed the file of any threats before it reached the victim. While the mechanisms of threat delivery worked, the actual threat code had been removed in a foolproof process using Votiro’s patented Positive Selection® technology.
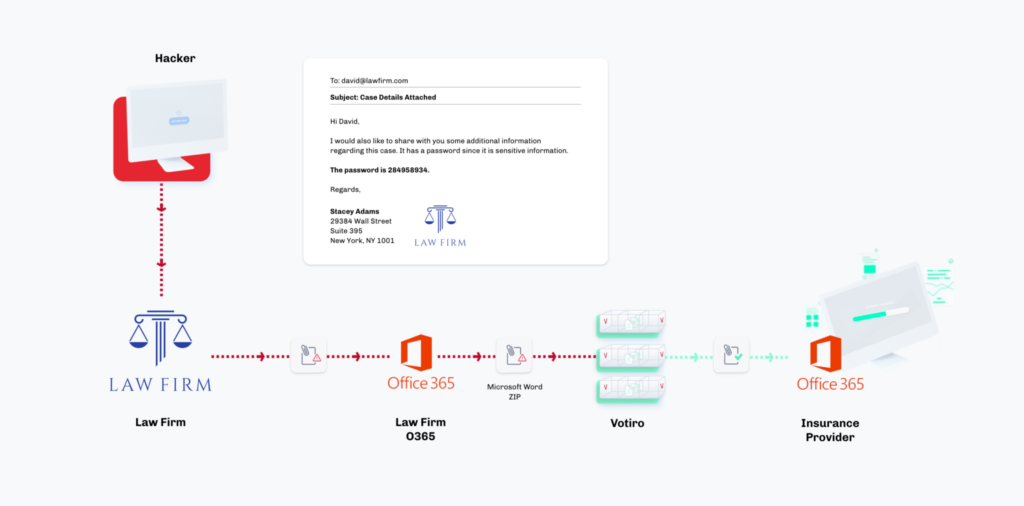
In this case, the employee received the malicious password-protected email and entered the ZIP file’s password into Votiro’s password-protected file portal. The portal exists in the same email that contained the ZIP file, so it did not interrupt the employee’s work or require intervention from the security team.
Votiro’s Positive Selection technology is a revolutionary approach to file security. Instead of seeking out and detecting known bad hashes, files, and code—which is never 100% accurate and would have missed this zero-day attack—Votiro only allows the known good content into a network. In this VEC, Votiro identified only the known good elements of the file, allowing those elements through to the end-user, leaving behind the malicious code. Therefore, the employee received a safe and secure file. (A useless file, as there were no promised legal documents inside, but a safe and secure file nonetheless!)
News you can use
Stay up-to-date on the latest industry news and get all the insights you need to navigate the cybersecurity world like a pro. It's as easy as using that form to the right. No catch. Just click, fill, subscribe, and sit back as the information comes to you.
Sign-up Here!
Subscribe to our newsletter for real-time insights about the cybersecurity industry.



