Votiro for
Secure File Transfer
Transfer files, not threats. Votiro enables businesses to safely transfer files via FTP, FTPS, SFTP, and SMB.
Votiro not only prevents hidden threats inside of incoming documents at-scale, it’s also capable of masking private data while files are still in-motion.
The open-API integrates seamlessly with existing technologies to prevent privacy risks and malware threats during simple and bulk file transfers — without slowing down automated processes or interrupting business productivity.
 Why Votiro for secure file transfer?
Why Votiro for secure file transfer?
Zero training required
Seamless integrations with everything
Works in cloud and on-premise
Implementation in as fast as 10 minutes
Don’t second-guess your next file transfer.
As with all our security solutions, Votiro adopts a Zero Trust approach to file transfers – no matter where the files come from. After all, in order to transfer files safely, you need to be sure that the content you’re receiving is free from malware and ransomware. However, current solutions such as AV and sandboxing leave gaps behind that can introduce malware and privacy risks.
To ensure your file transfers are safe and sound, our patented Positive Selection® technology sanitizes every file before it hits the FTP, FTPS, SFTP, SMB, and/or local folders.
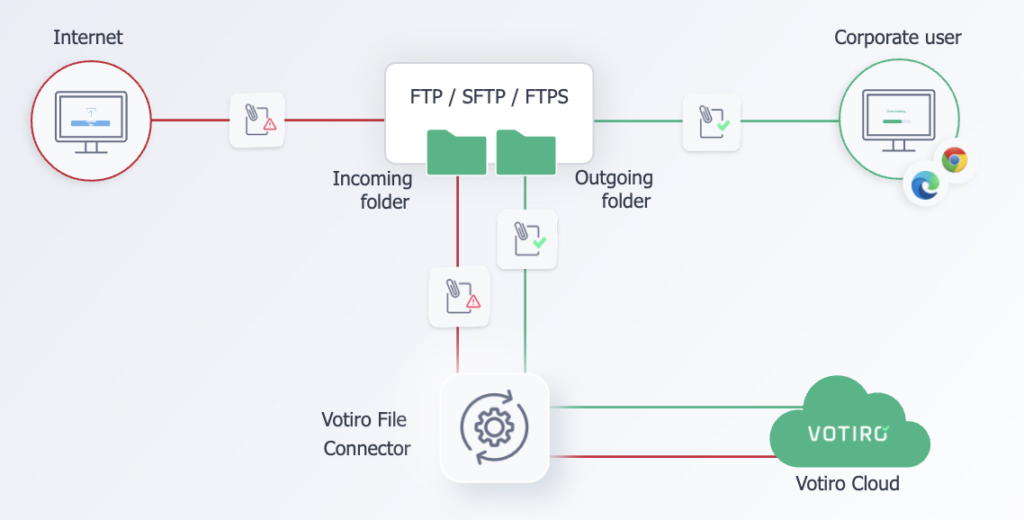

Votiro’s data security solution does what others can’t.
A compromised file transfer can open the door to endless headaches and repercussions for any business – including private data leaks and ransomware that can cost upwards of two-million dollars. That’s why it’s imperative that all your digital transfers are free of malicious elements and prying eyes. By taking a two-sided approach to Data Security in the form of Zero Trust Data Detection & Response, we allow organizations to stay protected from malware and privacy risks without resorting to multiple solutions.
At Votiro, we make certain that all files are verified as safe and that even the most evasive file-borne malware won’t make it through your entry points.
See Votiro DDR in Action
Book a live demo to see how Votiro Data Detection and Response can keep your organization safe and compliant with real-time data masking and proactive malware prevention.