Votiro for
Secure Data Storage
& File Transfers
Protect the information inside your data lakes and data storage environments from privacy risks and malware threats while also securing them in transit via FTP, FTPS, SFTP, and SMB.
Your data lake is secure and all your information is stored and exactly where you need it to be. Or so you think. Just like a water treatment plant keeps pollution out of real lakes, you’ll need to keep pollution out of your data lakes – starting from the moment files are being transferred.
Votiro prevents private data exfiltration and known and unknown threats from poisoning your digital storage locations – without ever slowing down business. Votiro also prevents hidden threats inside of incoming documents at-scale with the ability to mask private data while files are still in-motion.
 Why Votiro for your data lake & file transfer security?
Why Votiro for your data lake & file transfer security?
Zero training required
Seamless integrations with everything
Works in cloud and on-premise
Implementation in as fast as 10 minutes
How many sources of data populate your data lake?
Your data lake becomes more valuable the more integrated it is, but it also becomes more susceptible to risk of cyberattacks. So, while you may trust the files and content your team adds to your data lake, can you say the same about third parties uploading their own?
Malicious actors can upload file-borne threats to your data lake that can infect the entire ecosystem – sometimes remaining hidden for long periods of time until traditional security solutions like AV finally recognize them. Not only can this leave you open to malware and ransomware, but you’ll be at risk of non-compliance when it comes to private data regulations such as PII, PHI, and PCI.
With so much data on the line, both yours and that of connected vendors (as well as during M&A), Votiro allows you to better govern and protect all your stored data, seamlessly and at scale.
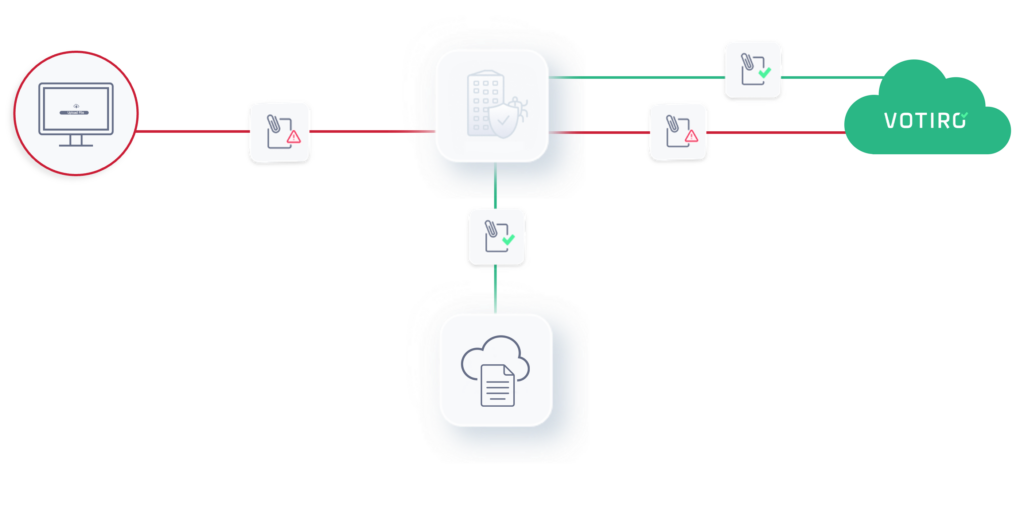
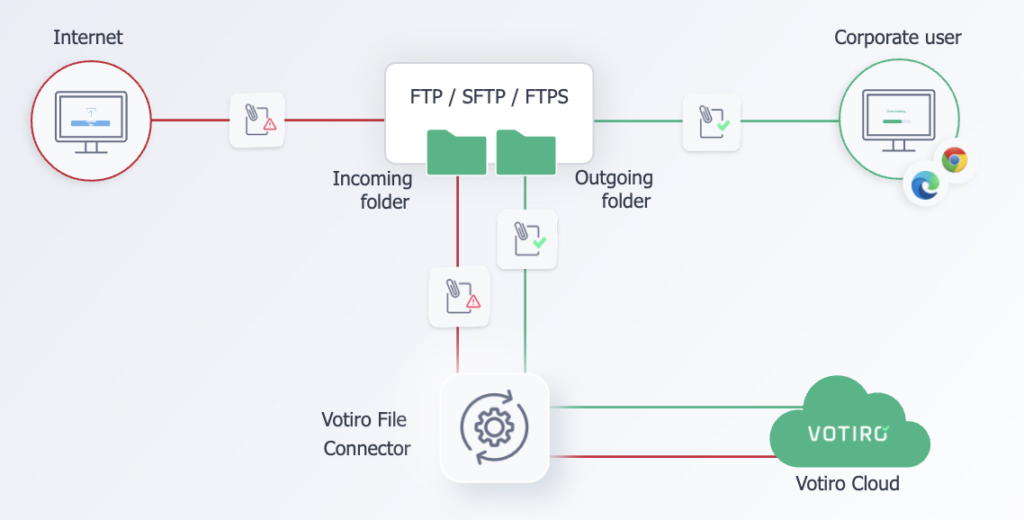
Don’t second-guess your next file transfer.
As with all our security solutions, Votiro adopts a Zero Trust approach to file transfers – no matter where the files come from. After all, in order to transfer files safely, you need to be sure that the content you’re receiving is free from malware and ransomware. However, current solutions such as AV and sandboxing leave gaps behind that can introduce malware and privacy risks.
To ensure your file transfers are safe and sound, our patented Positive Selection® technology sanitizes every file before it hits the FTP, FTPS, SFTP, SMB, and/or local folders.
Detection-based solutions can’t prevent unknown threats hiding in your data storage.
Even if you’ve scanned everything that enters your cloud environment, you can never be sure that a novel, zero-day threat hasn’t made its way inside, polluting the rest. You want to be sure that all digital assets and files are free of malicious elements and that even the most evasive malware won’t make it through.
With so many files in the mix, including those with sensitive information you don’t want exposed to the wrong person or vendor, Votiro ensures that you won’t have to think twice about what’s inside your data lake.


Votiro’s data security solution does what others can’t.
A compromised file transfer can open the door to endless headaches and repercussions for any business – including private data leaks and ransomware that can cost upwards of two-million dollars. That’s why it’s imperative that all your digital transfers are free of malicious elements and prying eyes. By taking a two-sided approach to Data Security in the form of Zero Trust Data Detection & Response, we allow organizations to stay protected from malware and privacy risks without resorting to multiple solutions.
At Votiro, we make certain that all files are verified as safe and that even the most evasive file-borne malware won’t make it through your entry points.
See Votiro DDR in Action
Book a live demo to see how Votiro Data Detection and Response can keep your organization safe and compliant with real-time data masking and proactive malware prevention.