Secure File Transfer
Votiro and
Owl Cyber Defense
Secure Government Ministry Networks
Owl & Votiro Partner to Secure Government Networks
Owl and Votiro have partnered to enable government ministries to securely transfer files into secure government networks. Votiro also provides the ability to analyze all files and prevent unauthorized known or unknown threats from entering the secure network. Owl data diodes and cross-domain solutions provide hardware-enforced, secure, one-way data transfers into secure networks.
Better Together: Votiro & Owl Cyber Defense
Securely Receive Files
from Third Parties via a web page to an IT network.
Securely Transfer Data
from an IT network to an isolated government network.
Get Safe Collaboration
Securely transfer financial files from bank clients to a secure collaboration system.
The challenge: Securely transferring files into a secure network.
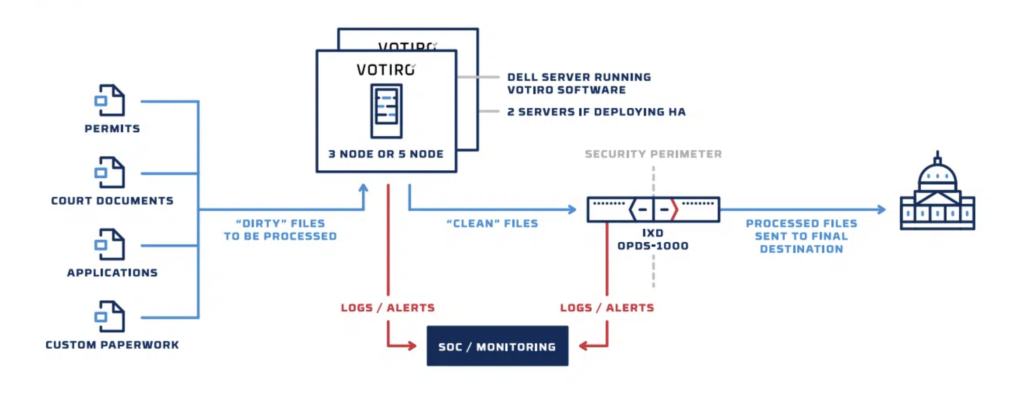
In order to perform their duties in serving the public, government ministries receive large numbers of files, applications, permits, and other documents every day. Whether intentional or not, these files represent a cybersecurity risk to the internal operations of each ministry processing these documents. It is essential for ministries to have confidence in the security of the files they are receiving.

An all-in-one solution
Votiro is built into Owl’s all-in-one data diode and cross-domain solutions, which is sold exclusively through Owl. This solution does not require end users to interact with Votiro. Some use cases include:
Securely receiving files like contracts, engineering drawings, and medical claims from a third party via a web page to an IT network.
Securely transferring confidential data, MS office, archives, and cybersecurity feeds from an IT network to an isolated government network.
Securely transferring financial files from bank clients to a secure collaboration system.
See Votiro DDR in Action
Book a live demo to see how Votiro Data Detection and Response can keep your organization safe and compliant with real-time data masking and proactive malware prevention.