Secure File Downloads
Votiro +
Zscaler
Download Content from the Web without Compromising on Security, Productivity, or File Fidelity
Eliminate the Risk of File-borne Malware, Data Breaches, and Other Malicious Attempts
Working together, Zscaler Browser Isolation and Votiro Data Detection & Response (DDR) make for a total security solution for file downloads via the web.
Both platforms run on Zero Trust principles to ensure that users can download the content they need — seamlessly, in real-time, without hindering productivity and maintaining file functionality and quality.
The Benefits of Votiro + Zscaler
Reduce Risk
By sanitizing every file passing through Zscaler’s Browser Isolation, organizations can reduce the risk of cyber attacks.
Scalability
As cloud-based solutions,
organizations can scale traffic and file ingestion based on workload needs, allowing for continuous business flow.
Zero Trust
Every file downloaded – no matter the source – is treated as a potential threat and sanitized automatically, with the option to mask data.
Traditional Security Solutions Are Not Enough
In the evolving ‘Work From Anywhere’ model, employees and third-parties are increasingly downloading, uploading, collaborating, and sharing content online. Which means, security teams are constantly challenged with keeping environments safe while managing countless entry and end-points—all without impacting business workflows or negatively affecting employee productivity. AV, EDR, and other traditional tools can’t get the job done alone.
This means moving to more reliable threat prevention tools, like Votiro, that proactively stop known and unknown threats in their tracks. Best of all, files remain intact and help reduce the amount of false positives and endless alerts that eat up IT and SOC bandwidth.

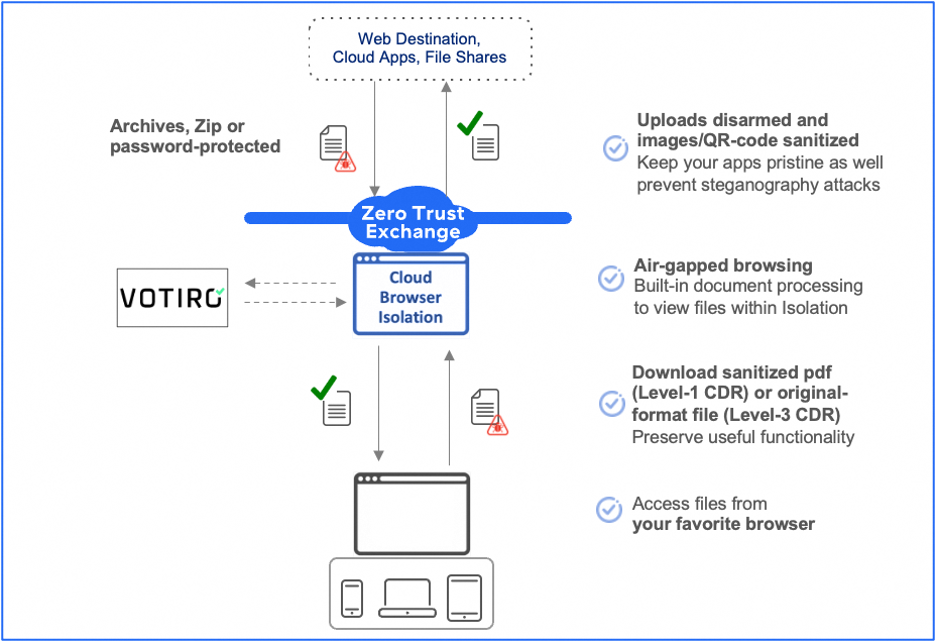
How Votiro + Zscaler Works
Votiro’s real-time Data Detection & Response platform allows files to safely flow in through Zscaler’s Browser Isolation (which is natively integrated within the company’s Zero Trust Exchange), reducing the amount of resources spent on removing files from quarantine or the time it takes to un-block files. The result is fully functional files, reduced risk, lower costs, and increased productivity for IT and end-users.
How Votiro + Zscaler Works – Continued
Together, the architecture entails regeneration of file content by stripping out potential threats and reconstructing only safe, known good content, ensuring the resulting original-format file is safe and fully functional for end users and apps to use (Level-3 CDR). This means you can edit a Word document or build over the data model within an Excel file or a financial planning workbook. Same can be done for archives, images, zipped and password-protected files.
See Votiro DDR in Action
Book a live demo to see how Votiro Data Detection and Response can keep your organization safe and compliant with real-time data masking and proactive malware prevention.