Secure Web Browsing
Safe File Downloads with CyberArk
Organizations gain a secure and feature-rich browsing experience tailored for the enterprise.
Security-First Protection for Web-Based Threats
By combining the strengths of CyberArk Secure Browser and Votiro’s Zero Trust Data Detection and Response (DDR), organizations can establish a robust, multi-layered defense that fortifies their cyber resilience and safeguards their digital assets. This integrated solution not only mitigates the risks associated with browser-based attacks but also neutralizes the threats posed by malicious file content, ensuring a safe and secure digital environment for employees and stakeholders.
How Votiro & CyberArk Secure the Browser Experience
Security-First Design
CyberArk is designed to deliver a secure browsing experience. Combined with Votiro, this defense-in-depth solution allows organizations to proactively prevent zero-day exploits.
Granular Access Controls
CyberArk enforces granular access controls to sensitive business applications, and provides visibility into user activity, while maintaining a seamless and productive user experience.
True File Sanitization
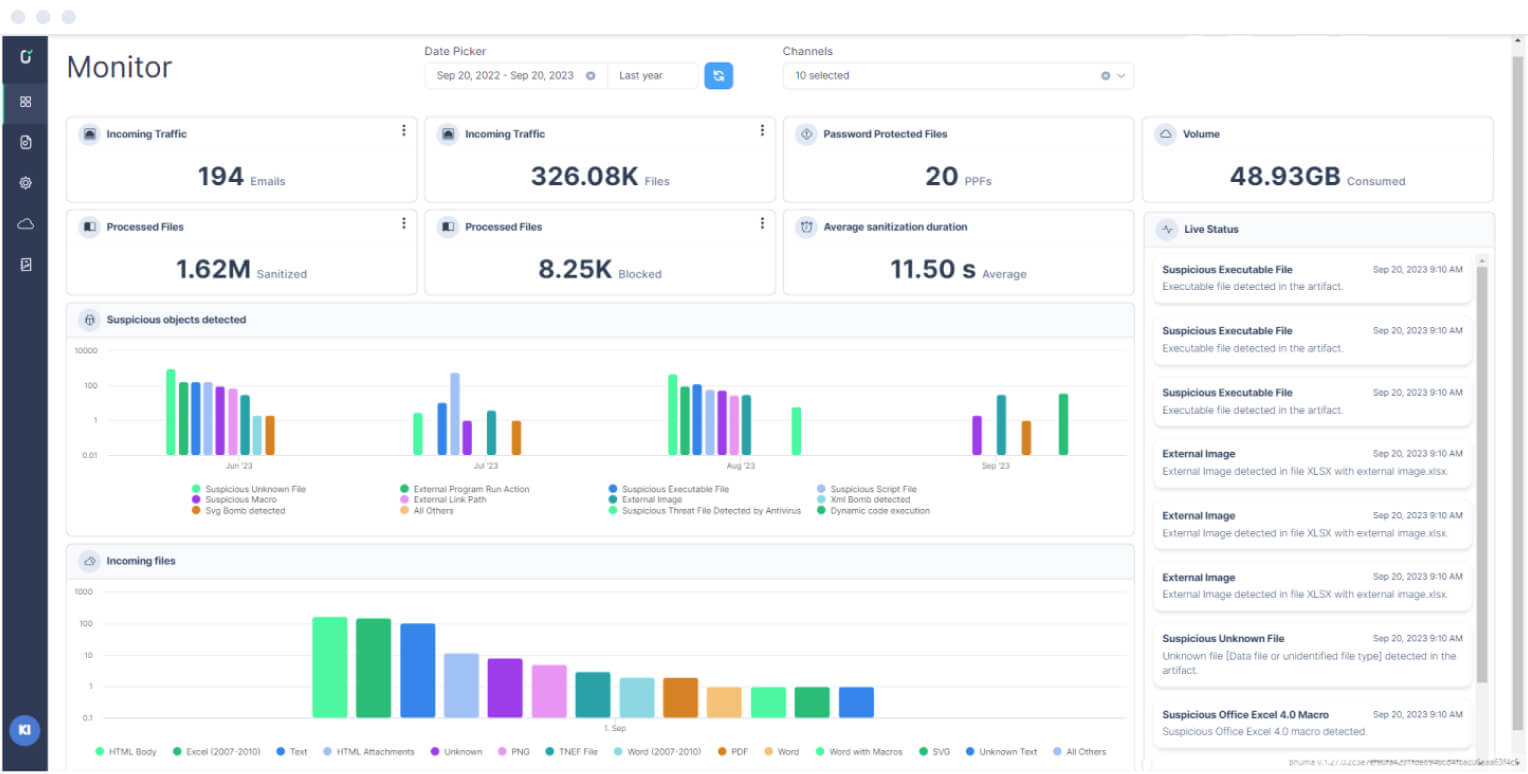
Votiro’s open-API sanitizes all incoming files quickly by extracting all clean content and creating a safe, fully functional file, ensuring a safe web browsing experience for multiple end-users.
More than just protection from malware threats.
Complementing CyberArk’s Secure Browser, Votiro’s Zero Trust Data Detection and Response platform provides real-time privacy and compliance monitoring, actionable data insights, and seamless integration with existing security infrastructure.

Just a few easy steps to enable secure web browsing.
CyberArk and Votiro make installing the browser extension a simple and stress-free process. In just four steps, organizations can integrate Votiro and start protecting their environment from malicious browser downloads.
See Votiro DDR in Action
Book a live demo to see how Votiro Data Detection and Response can keep your organization safe and compliant with real-time data masking and proactive malware prevention.