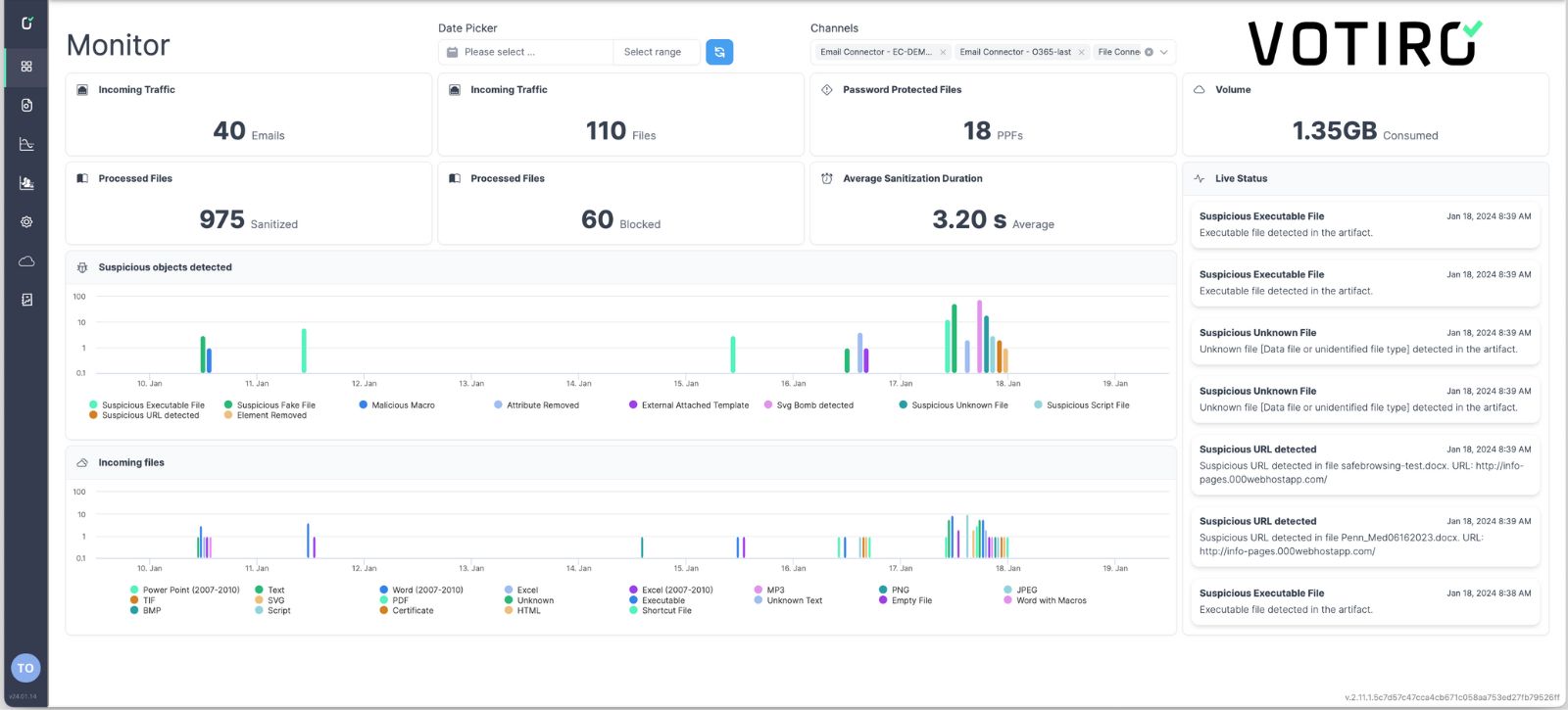
Welcome to Real-time Zero Trust Data Security.
Votiro’s Zero Trust Data Security solution has ensured the continuous and quick delivery of safe and compliant content being downloaded, shared, and uploaded from systems all over the globe—to the tune of over 10 billion files with zero breaches to report.
As businesses and threat actors alike continue to adopt GenAI en masse, cyber threats have begun to evolve rapidly, resulting in sensitive data exfiltration to go largely undetected and or unmonitored. As a result, modern data security requires a two-fold approach.
Votiro is meeting the challenges to data security in the form of advanced Data Detection and Response (DDR). Bringing active data masking and proactive content disarm and reconstruction (CDR) under one unified platform, organizations have access to a two-fold security solution that enables them to disarm threats and mask sensitive, unstructured data in real time. Now, IT and SOCs can keep data compliant with complex privacy regulations—and simultaneously safe from known and unknown threats.
Behind the Scenes of our Data Masking and File Sanitization Process
Four Steps to Safe and Secure Data
01
Step 1
Votiro intercepts files with potential data privacy risks and hidden malware threats – in real time.
02
Step 2
Votiro intelligently dissects files into content, objects, and templates — only trusting known-good elements while also discovering and detecting private data (PII, PCI, PHI).
03
Step 3
File content is quickly rebuilt on new, safe templates (leaving malware behind) while masking private data based on fine-grained security policies.
04
Step 4
A. 100% safe, fully functional file is delivered.
B. Private data is masked for use by approved users only.
C. Synthetic, masked data can be generated for training GenAI apps.
As pioneers of Zero Trust Content Security, Votiro has dedicated the last decade effectively protecting organizations from malware breaches. Today, we go beyond a myriad of existing point solutions to provide threat prevention and data security in a single, unified platform.
Zero Trust means we ensure every single file is examined and sanitized accordingly, no matter what.
Our sophisticated Data Detection and Response platform extends this protection to the real-time masking of sensitive information while it’s still in motion. This seamless process of discovering, detecting, and masking data has ensured that only authorized users, AI systems, and third-party vendors get access to personally identifiable information (PII) including PCI and PHI.
the rest…
While useful for gaining insights on data security risks, Data Security Posture Management typically identifies vulnerabilities and manages risks passively, meaning mitigation can be critically delayed.
Data Loss Protection tools monitor and outright block sensitive data based on predefined rules, effectively preventing unauthorized transmission or access after detection. This significantly lessens productivity within organizations.
Predictions based on a signature-based list or collaborative database, which leaves room for zero-day threats to breach your endpoints.
Virtualization aimed at predicting outbreaks but severely slows down productivity and can still allow malware to sneak through.
(EDR/MDR/XDR)
Reactive tools that highlight threats that have already reached the endpoint and alerts for after-the-fact mitigation — which is far too late for true protection.
Votiro’s Two-fold Data Security Solution
Active Data Masking for Privacy & Compliance
Going beyond reactive tools that allow data breaches to take hold of sensitive data, Votiro provides organizations with in-motion data masking for both unstructured and structured data alike. This proactive approach ensures only authorized users have access to the data they need.
Proactive File Sanitization Using Advanced CDR
While other CDR providers rely on malware detection, known signatures, and predictive analysis, Votiro’s Positive Selection® technology delivers fully functional content in just milliseconds, ensuring prevention of zero-day attacks with a 0% false positive rate.
See how Votiro delivers real-time data security.
Schedule a personalized demo to learn how our Zero Trust Data Detection & Response platform protects private data and eliminates file-borne threats.