WhatsApp Phishing Attack Targets International Hospitality & Tourism Industry

Votiro was made aware of a new phishing attack when a hotel employee received a password-protected zip file from an unknown contact via WhatsApp on her work mobile. This method of attack is not surprising, considering that WhatsApp’s billions-strong user base makes it a frequent target of hackers.
More Channels, Same Threats
Today, it has become increasingly common for businesses to engage with customers over multiple communication channels, including WhatsApp. For many hotels, WhatsApp is the channel of choice due to its incredibly high 98% open rate and conversational messaging that makes interactions feel natural and builds trust between the customer and the business. For example, when OYO Hotels & Homes, the third-largest hotel chain in the world, switched to WhatsApp, they saw more than 85,000 monthly conversions, 55,000 monthly unique users engaged, and a 15% reduction in call center traffic.
As omni-channel approaches to customer service increase, threat actors continue to take advantage of these channels – often targeting staff that field requests from guests located all across the globe, thus removing the typical red flags associated with phishing attempts. According to a report by Ponemon and IBM Security, the average total cost of a data breach in the hospitality industry is $2.94 million – making cybersecurity a top requirement for CISOs and IT teams that work in the field.
This article will highlight a specific example of a threat actor attempting to use the hospitality industry’s dedication to service to the actor’s advantage.
The Phishing Attempt
In this instance, the hacker booked a room at an international hotel and submitted a request for the hotel to get in touch with them immediately via WhatsApp about an urgent issue. Once the hotel employee engaged the customer over WhatsApp, the hacker responded with their request.
The WhatsApp message looked innocent enough (it even had a “waving woman” emoji in it). It read:
Hello! ♀️
I will come to visit you soon and would like to ask for your help. I have run into an allergy problem so I would be very grateful if you could review my list of allergies.
The file won’t open on the phone because it’s in the zip folder. I’m on a train and I just can’t open the file any other way.
Thank you for your concern and willingness to help me. I really appreciate your time and efforts that you put in to make my stay at your place as comfortable as possible.
Folder password: 1111”
Attached on the Whatsapp message thread was a malicious zip file: WwDocs.pdf.zip.

The malicious actors knew that the weaponized files would not open on an iPhone, and therefore lured their victims to open the weaponized file via WhatsApp Web, which is installed on many office workstations.
Unfortunately, the employee unknowingly clicked on the weaponized file, input the password, and opened it, potentially exposing the entire hotel network to the hacker’s nefarious plans. Files of this nature can infect the hotel’s computer systems and hold the data for ransom, shut down the security systems to enable a break-in, or lock the reservation system to cause revenue-based damage. As such, the risk was enormous.
Plugin Protection
Now, if the hotel had been protected by the Votiro Web Browser Plugin, the malicious file would have been sanitized automatically. For instance, when the employee extracted the content of the archive, the suspicious element inside the zip would have been proactively identified as a trojan stealer that aimed to steal credentials and other personal information. Without a plugin in place, the trojan could potentially download additional malware to the endpoint and cause even more damage to the hotel and its reputation with tourists.
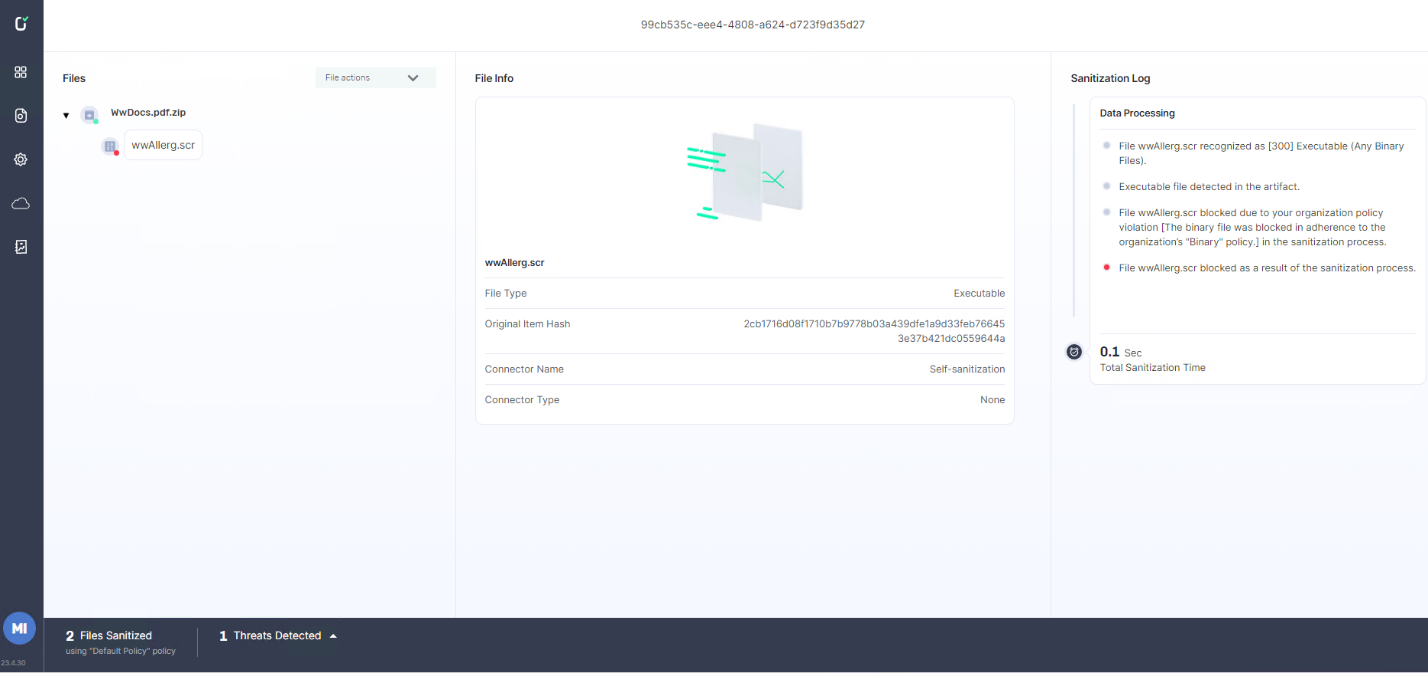
What Was Inside the Zip File?
Because the phishing attempt was brought to the attention of a Votiro employee, they were able to independently process and analyze the file to see how it worked – and learn what Votiro could have done to prevent the attack from ever making it to the endpoint.
With Votiro’s ability to analyze each of the files sanitized, it was revealed that the malicious file inside the password-protected document was a .SCR file named wwAllerg.SCR – a file that was already identified by the cybersecurity community as weaponized. However, even though the computer’s antivirus didn’t flag the file as a known malware, since the .SCR (binary screen-saver file type) is considered a binary, it would have been blocked due to Votiro’s policy that prevents executables and other binary files.

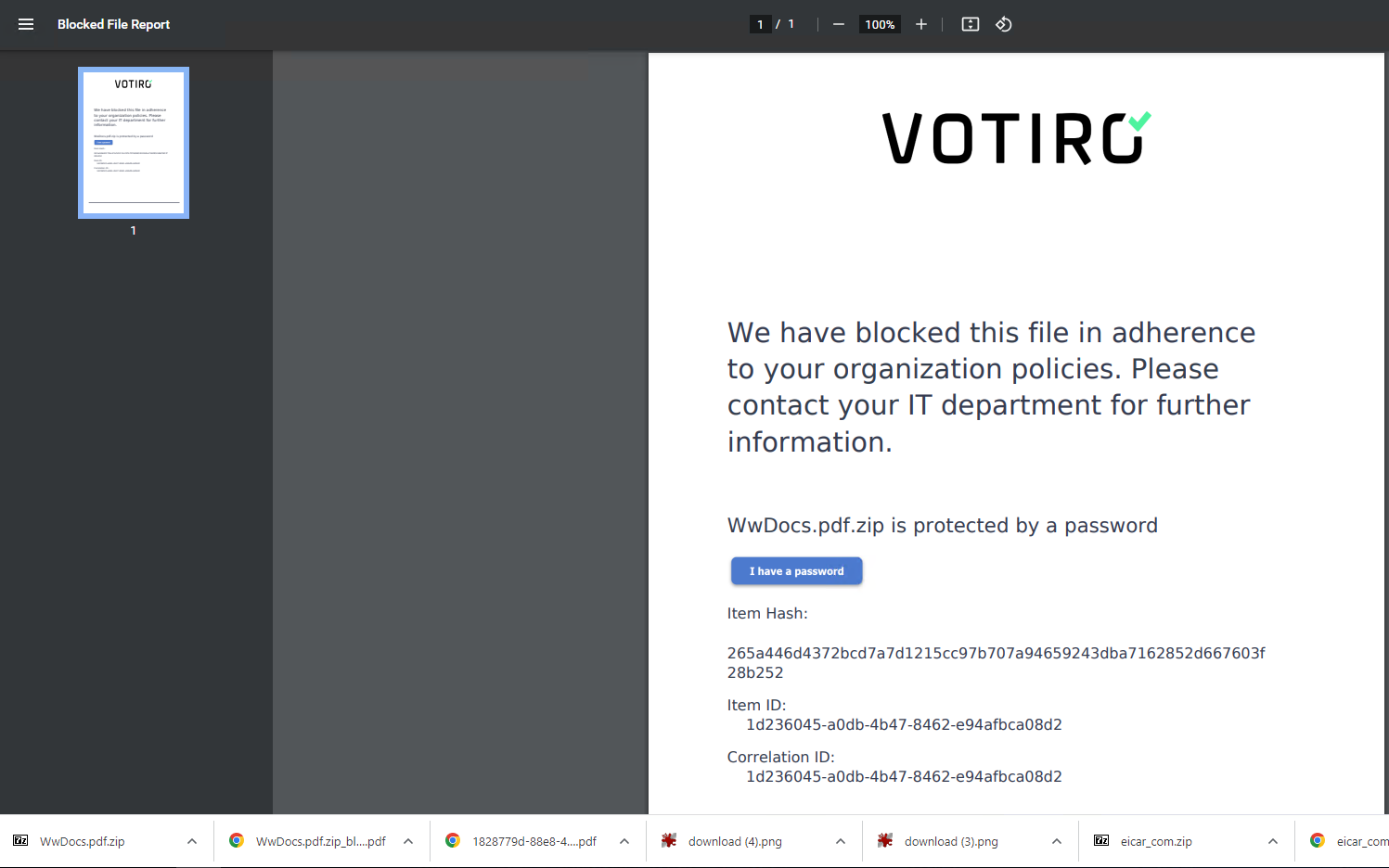
Votiro’s system immediately recognized the file as password protected and blocked the suspicious element in the zip, which would have effectively saved the hotel (and its employee) from significant harm. The file could then be replaced with a branded template that indicates to the employee that the file did not follow the security policy of the hotel and therefore was blocked as a result.
Get Votiro Protection
Votiro’s API-centric solution effortlessly integrates into existing business workflows, enabling organizations to instantly benefit from protection against cyber threats, like the one above. Implementation times are impressively quick, and companies see value right away as Votiro begins sanitizing files.
Contact us today to learn more about how Votiro leads the way in preventing hidden threats in files, and securing your organization while maintaining productivity. And if you’re ready to try Votiro for yourself, start today with a free 30-day trial.
News you can use
Stay up-to-date on the latest industry news and get all the insights you need to navigate the cybersecurity world like a pro. It's as easy as using that form to the right. No catch. Just click, fill, subscribe, and sit back as the information comes to you.
Sign-up Here!
Subscribe to our newsletter for real-time insights about the cybersecurity industry.



