Votiro’s Proven Protection: Retroscan for Zero-Day Threats

On any given day, a seemingly harmless file may enter your organization, sometimes via your email system, bypassing every layer of traditional defense you’ve paid for and put into place. We’ve seen it before: an antivirus scan clears an innocuous attachment and the file is passed along as ‘safe.’ Then, days, weeks, or even months later, that same file is identified as malicious—its zero-day payload finally flagged after the virus definitions update. As we all know, by that point the damage is already done.
This scenario is not hypothetical; it’s the reality of dealing with zero-day threats. Cybercriminals exploit the lag between attack and detection, embedding harmful code in files that appear normal to traditional defenses. Based on the amount of breaches that are reported each and every year, these zero-day attacks have become a significant challenge, leaving organizations scrambling to respond to threats they didn’t see coming.
Why We Need a Window Into Past Threats
For decades, traditional security defenses have operated like sentinels with a fixed rulebook—relying on virus definitions and known threat signatures to detect and block malicious content hidden within sends. A solution that’s worth the investment when the threat has previously been recorded. Yet, without a pre-existing signature, zero-day threats can easily bypass standard defenses and enter organizational systems undetected. A nightmare scenario for internal team members simply trying to do their jobs – and one that creates a dangerous gap in security.
As many in the cybersecurity field can attest, hindsight isn’t just about understanding what went wrong—it’s about proving what went right. Organizations need a way to defend against unseen dangers and validate the effectiveness of their proactive measures before budget time rolls around. This is where having a “window to the past” becomes invaluable, allowing security teams to revisit files and retroactively confirm that hidden threats were neutralized before they could strike. For Votiro customers, this window is known as Retroscan. But more on that in a moment.
The Role of CDR in Preemptive Protection
Votiro’s advanced Content Disarm and Reconstruction (CDR) technology takes a radically proactive approach to file security, neutralizing threats before they have a chance to execute. Unlike traditional defenses (i.e., DLP, EDR) that rely on detection-based approaches, CDR operates under the assumption that all files are already compromised—even those that appear entirely benign or ones that have been deemed safe in the past. By deconstructing each incoming file, stripping out potentially harmful elements like malicious macros or embedded scripts, then reconstructing them into safe, functional versions, Votiro ensures that every file is sanitized before the point of entry – without causing unnecessary stress for IT teams, overwhelming SOCs, or hindering workspace productivity.
Proving CDR Effectiveness with Retroscan
Retroscan is a staple of the Votiro platform, providing critical evidence that proactive CDR protection is effective and indispensable. It operates by re-evaluating files that have already been sanitized by Votiro against updated antivirus definitions. This means that even when a zero-day threat initially bypasses traditional defenses (yet is made safe by Votiro), Retroscan can retroactively confirm that the threat was present and that it was Votiro’s CDR that ensured it was eliminated before it could cause harm.
Beyond this functionality’s ability to build confidence, the process reassures organizations that their files remain secure even in the face of evolving cybersecurity risks, such as GenAI-assisted phishing. With proof of ROI and continuous monitoring, security teams can use the provided data and insights to prepare for changes in attack methodologies, make more informed policy decisions, and bolster their overall security posture.
An Example of Retroscan in Action
In this case study, we demonstrate how Retroscan identified a malicious file missed by traditional email defenses and prove how Votiro’s CDR technology safeguarded the Organization.
What Happened: The file in question entered the Organization’s email system and was flagged as safe by traditional defenses that relied on outdated virus definitions and detection mechanisms. Despite the file appearing benign, Votiro’s CDR automatically identified, sanitized, and rebuilt the file. This removed hidden and potentially harmful elements before being sent safely to the endpoint.
Image 1: The File’s Entry
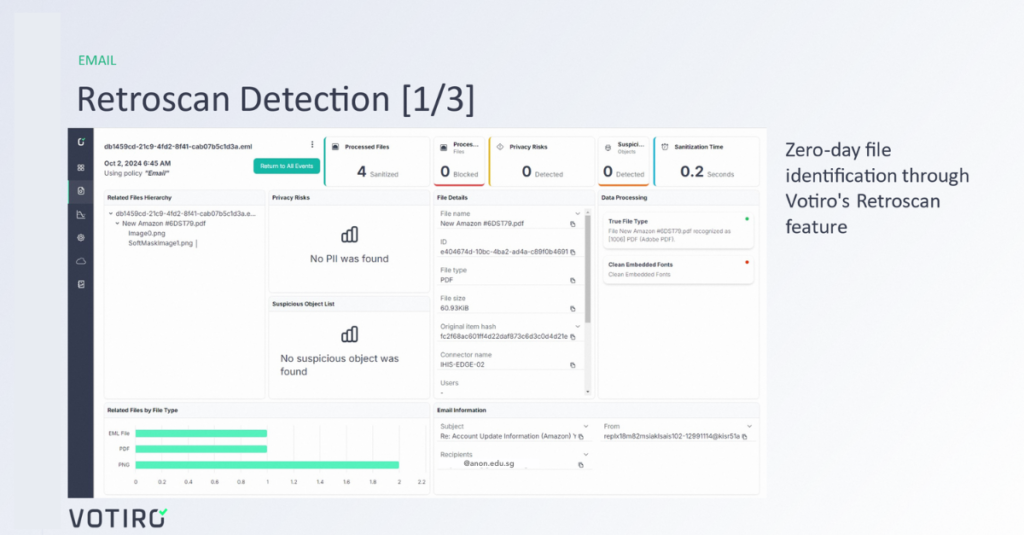
Days later, antivirus definitions were updated. At this point, Retroscan was able to re-evaluate the previously sanitized file. Retroscan then confirmed that the original file contained malicious elements, which those traditional defenses failed to detect.
Image 2: Retroscan Validates the Threat
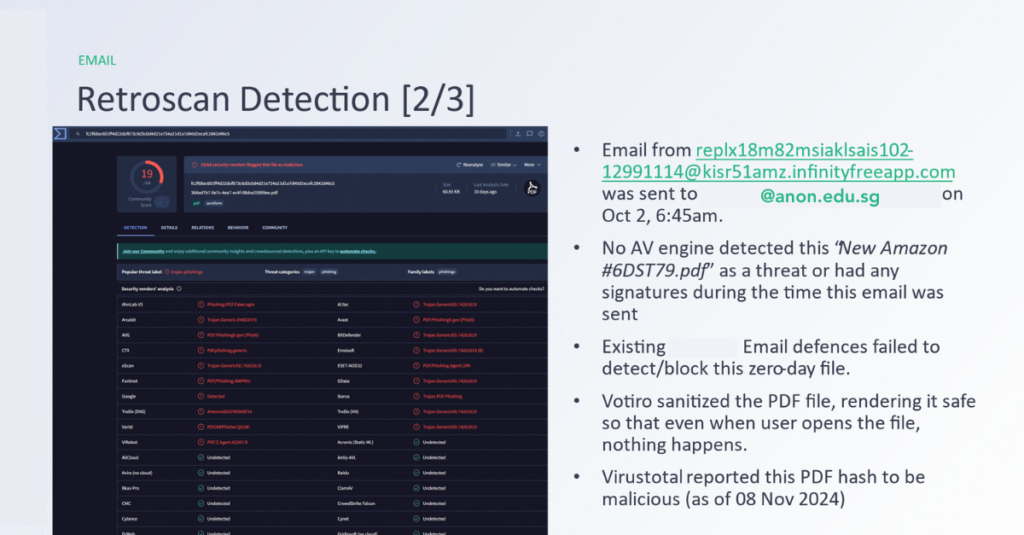
The sanitized version of the file, processed by Votiro’s CDR, was re-evaluated alongside the original. The comparison showed that the Votiro-protected file was entirely safe, free from the hidden malicious elements that would have posed a significant risk had they gone undetected.
Image 3: The Safe Outcome
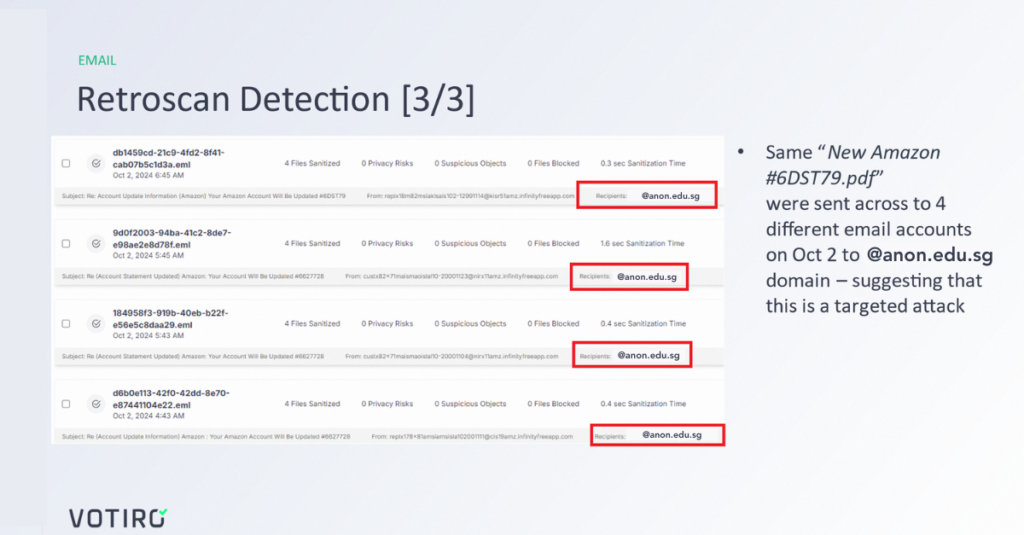
The Benefits of Retroscan
- Retroscan provides tangible evidence for security teams that Votiro’s CDR technology effectively neutralizes unknown threats, even when traditional defenses fail. This validation equips teams with the confidence to demonstrate their organization’s security efficacy to stakeholders, regulatory bodies, and auditors. By offering a clear record of preemptive action against zero-day threats, Retroscan helps bolster compliance efforts and supports a robust cybersecurity posture.
- Retroscan identifies patterns in missed threats and provides valuable insights that enable security teams to refine their defenses further. This improved threat intelligence helps organizations stay ahead of attackers by adapting to new techniques and vulnerabilities as they emerge, creating a more resilient security environment.
- Retroscan builds trust in proactive security measures across technical teams and leadership, assuring organizations that their investment in advanced threat protection is not just theoretical but a proven safeguard against the unpredictable nature of modern cyber threats. As a result, this saves teams money by consolidating redundant tools, reduces false positives and the accompanying noise in the SOC, and eliminates the stress that comes with manual mitigation process like quarantining and sandboxing.
Are You Ready For the Next Zero-Day?
Zero-day threats are an ever-present risk, challenging traditional security defenses at every turn. Combined with retrospective analysis, Votiro doesn’t just stop threats—it proves platform effectiveness, providing security teams with the confidence and evidence they need to defend against even the most sophisticated attacks.
And Votiro doesn’t stop there. Advanced CDR is just one side of the data security equation that Votiro is solving with its Zero Trust Data Detection and Response (DDR) platform. Votiro DDR also ensures that sensitive data (i.e., PII, PCI, PHI) is discovered, identified, and masked before it’s inadvertently shared with unapproved parties or storage locations. Which means, organizations can safeguard their data compliance standings and reduce data exposure risks from one unified platform.
Experience the power of proactive security and retrospective validation by scheduling a demo of Votiro’s intelligent, defense-in-depth data security solution. The next zero-day could be around the corner—let’s make sure you’re prepared.
News you can use
Stay up-to-date on the latest industry news and get all the insights you need to navigate the cybersecurity world like a pro. It's as easy as using that form to the right. No catch. Just click, fill, subscribe, and sit back as the information comes to you.
Sign-up Here!
Subscribe to our newsletter for real-time insights about the cybersecurity industry.