The Scourge of Ransomware
Combating Ransomware in the Healthcare Industry
The first few months of 2016 have turned out to be quite fruitful for malicious groups and individuals launching ransomware attacks. Among the organizations that have been hit are the New York Times, the BBC, the NFL, and AOL. Although this type of attack has always been a favorite tool among hackers, the rise of “ransomware as a service” (RaaS) has enabled even non-hackers to buy ransomware kits on the Darknet for as little as $39 (according to a Forbes article by Kevin Murnane) and deploy the malware in any organization.
What is Ransomware?
Ransomware is malicious software that when activated, locks the victim’s computer or encrypts the files in the computer. To regain access, the victim must pay a ransom to the hacker who injected the ransomware. One of the most popular types of ransomware among today’s cybercriminals is Cryptolocker, which encrypts a victim’s files. Only after paying a ransom does the victim obtain the decryption key for unlocking the files. Several ransomware removal tools are available online, but most of them are useless, especially on newer types of ransomware.
The Cost of Ransomware
According to a 2015 report from the Cyber Threat Alliance, CryptoWall ransomware was accountable for $325 million in damages in 2015.
Losses from a ransomware attack don’t stop with the ransom itself. In a 2016 attack, Hollywood Presbyterian Medical Center was forced to pay $17,000 in Bitcoin to regain access to its files. However, the other costs involved in such an incident can easily surpass the ransom that is paid. Citing InfoSec Institute, Brad Brooks notes that “the cost of a computer forensic investigation varies greatly ($100-$600 per hour), depending on the number and types of systems involved and the complexity of the recovery of evidence.” Add to that the financial harm stemming from the system’s downtime, the loss of current and future customers because of the organization’s damaged reputation, and the outlay required for patching the vulnerabilities in the system. In the end, a ransomware attack might end up costing an organization hundreds of thousands of dollars!
How Do You Get Infected by Ransomware?
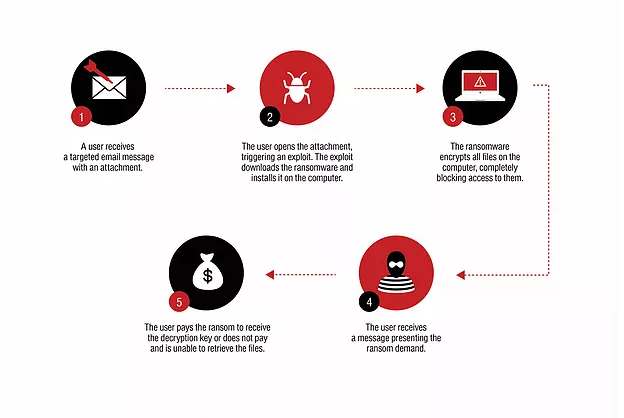
The most common way of getting infected by ransomware is via a targeted email attack—specifically, a spear-phishing email message. The message contains an attachment, perhaps a Microsoft Office or Adobe PDF file, from what appears to be a reliable source. A user who opens the attachment unintentionally triggers an exploit, which installs the ransomware in the computer.
What Can You Do if You are Attacked by Ransomware?
Unfortunately, there is not much you can do if ransomware penetrates your computer. Joseph Bonavolonta, assistant special agent in charge of the FBI’s cyber and counterintelligence program in its Boston office, remarked: “The ransomware is that good. To be honest, we often advise people just to pay the ransom.”
Is There Anything You Can Do to Avoid Ransomware Attacks?
Most companies focus on training employees to detect suspicious email, hoping that this method will protect the organization against attacks—but regardless of how good the training is, it is not one hundred percent foolproof. Most cybercriminals spend a massive amount of time building their attack campaigns based on social engineering, which practically guarantees that a user will open an infected attachment.
Furthermore, traditional security solutions are unequipped to deal with modern ransomware. Many organizations expect their antivirus software to detect and stop all types of cyber attacks. This strategy does not work because antivirus software relies on signatures to detect threats, whereas most ransomware, if not all, is signature-less. Sandbox solutions attempt to execute ransomware on their virtual machines, but today’s ransomware almost always incorporates sandbox evasion capabilities.
How Votiro Can Prevent Ransomware
The best way to prevent a ransomware attack is to disarm threats in advance. Votiro, with its patented content disarm and reconstruction (CDR) technology, removes harmful, unwanted code from email attachments and provides you with a safe-to-edit version of the attached files.
Because many new kinds of ransomware pop up every day, you need protection that does not rely on known threats or signatures, as do antivirus programs, but rather knows how to block undisclosed and zero-day threats—exactly what the Votiro technology does.
Votiro provides organizations with indispensable protection against the undisclosed and zero-day exploits used in cyber attacks. The robust processes and patented anti-exploit technology of Votiro cleanses incoming files from potential cyber threats. Banks, government agencies, utilities, telecommunications service providers, health organizations, and large enterprises around the world rely on Votiro solutions to protect their critical IT infrastructure and sensitive data.
News you can use
Stay up-to-date on the latest industry news and get all the insights you need to navigate the cybersecurity world like a pro. It's as easy as using that form to the right. No catch. Just click, fill, subscribe, and sit back as the information comes to you.
Sign-up Here!
Subscribe to our newsletter for real-time insights about the cybersecurity industry.



