The Myth of Multiscanning: More Isn’t Always Better
Cybersecurity often feels like more is better. More tools. More safeguards. More engines scanning every file that enters a system. That’s the promise behind multiscanning, an approach popularized by vendors that stack dozens of antivirus engines side by side, all scanning the same content for threats. On the surface, it sounds like a no-brainer. Why rely on one engine’s opinion when you can consult thirty?
These vendors present multiscanning as the ultimate safety net. Their messaging suggests that this method delivers nearly flawless detection rates, catching even the most obscure malware by casting a wide net. The appeal is clear: more engines working in parallel must mean more protection, right?
But under the hood, the reality is more complicated. While multiscanning may boost the numbers in a report, those numbers don’t tell the whole story. In practice, this approach often introduces redundancy, bloats the threat landscape with duplicate detections, and generates a surge of false positives. These side effects skew perceived efficacy and create real friction for IT teams. Instead of streamlining detection and response, multiscanning can slow it down, overwhelm analysts, and increase operational costs.
Decoding Multiscanning Claims
Proponents of multiscanning love to tout one number above all others: 99%. That’s the detection rate some vendors claim to reach by combining dozens of antivirus engines into a single platform. On paper, it looks like a slam dunk, a seemingly bulletproof way to catch malware before it breaches the perimeter. To further back these claims, some providers even publish detailed efficacy reports showing how detection rates climb with each additional engine added to the mix.
But this version of the story skips over the fine print.
These reports often rely on a deceptively simple equation: if five engines all flag the same file as malicious, that’s counted as five successful detections. That’s one threat identified by multiple sources, not five independent wins. The result? Inflated statistics that give the illusion of comprehensive coverage while masking the redundancy under the hood.
Worse still, the reports usually lack context. What types of malware were detected? How relevant are those threats in today’s environment? Were they already known to the engines in question? Were any zero days involved? Without this clarity, the numbers are just that—numbers. Impressive at a glance, they are often disconnected from the real-world performance that security teams actually need.
When security strategies are judged on how good they look in a PDF rather than how well they perform in a breach scenario, the focus shifts from practical protection to marketing theater. And that’s where multiscanning begins to unravel, not in its intent but in its execution.
The Pitfalls of Multiscanning
The promise of multiscanning might be alluring, but the trade-offs quickly reveal themselves once deployed in the real world. One of the most immediate and costly side effects is the surge in false positives. With so many engines evaluating the same file, each based on its own detection criteria and threat intelligence, it’s inevitable that they’ll occasionally disagree. What one engine considers suspicious, another might pass over entirely, and a third may flag it as malicious. Multiply that uncertainty across dozens of engines, resulting in an avalanche of alerts.
This doesn’t lead to more clarity. It leads to chaos.
Security teams are left to sift through duplicate warnings and conflicting assessments, often chasing phantom threats. This alert fatigue doesn’t just drain time, it erodes trust in the tools themselves. Over time, analysts become desensitized to alerts, increasing the risk of missing the real threats that matter. Many simply turn off these tools to get some peace and quiet, which means there’s no security at all.
Then comes the operational burden. Maintaining and tuning multiple antivirus engines isn’t just a checkbox exercise. Each one requires its own updates, configurations, policy rules, and integration points. When those engines don’t play nicely together, or their outputs flood the SIEM with conflicting data, teams are forced into hours of manual reconciliation. The complexity increases exponentially with scale.
Then, there’s the cost. 30 tools equals thirty budget line items. This means the only real alert teams will be getting is from the accounting team.
All of this has a cost in performance, too. When dozens of engines are scanning every file, latency creeps in. What should be a quick scan turns into a bottleneck. Files are held up in a queue. Users wait. Processes stall. For sectors like finance, healthcare, and critical infrastructure, where real-time data access is mission-critical, these delays aren’t just frustrating, they’re unacceptable.
Votiro’s Streamlined Approach to AV Scanning
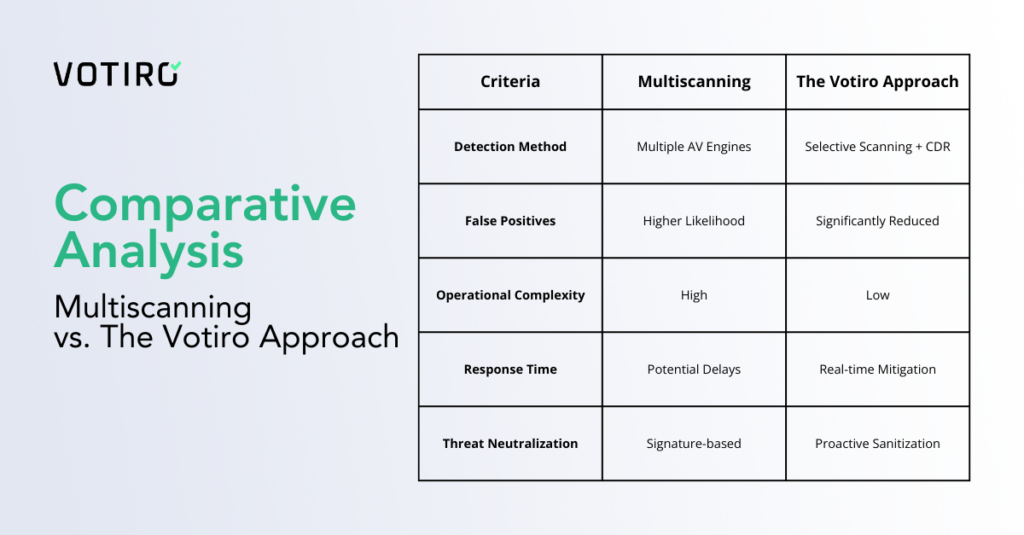
While some outfits continue to stack engine upon engine in pursuit of inflated detection stats, Votiro takes a different path, one built on precision, not noise. Instead of leaning toward the idea that more scanners equal better security, Votiro relies on two carefully selected tools, which are kept undisclosed for security purposes. This focused approach minimizes the chaos that comes with multiscanning: fewer false positives, faster processing, and a leaner security stack that’s easier to manage.
But that’s just the beginning.
Where traditional tools rely on spotting known threats, Votiro’s advanced Content Disarm and Reconstruction (CDR) technology shifts the paradigm. It doesn’t try to guess what might be dangerous, it assumes everything could be. Files entering the organization are automatically sanitized, stripped of embedded threats, and rebuilt from the ground up using only safe, verified elements—including safe macros. The result? Clean, fully functional files that retain their utility without carrying hidden payloads.
This isn’t detection theater. It’s prevention in action.
Votiro’s layered solution, Zero Trust Data Detection & Response (DDR), isn’t about hoping threats are caught after they appear, it’s about eliminating them in transit. Whether it’s malware embedded in a document or sensitive data leaking through an outbound file, Votiro steps in before the risk ever lands. Files are sanitized. Sensitive information is masked. And operations continue uninterrupted.
It’s a quiet kind of security. One that doesn’t flood dashboards with alerts or bog systems down in processing queues. Votiro’s model focuses on delivering certainty, not just signals, so teams can spend less time managing noise and more time moving the business forward.
Rethinking Malware Detection Strategies
Multiscanning paints a compelling picture, one where more engines mean more protection and bigger detection nets ensure nothing slips through. But beneath the surface, this approach often creates more problems than it solves. The sheer volume of redundant alerts, the operational strain of maintaining so many moving parts, and the delays introduced into everyday workflows all add up.
That’s why it’s time to rethink what effective malware protection really looks like.
Modern threats don’t care how many antivirus engines are lined up to scan them. What organizations need today is not just broader detection but smarter prevention. They need technology that disarms threats at the source, preserves file usability, and reduces the load on already stretched IT teams. By focusing on real-time file sanitization that has antivirus baked in, Votiro eliminates threats before they become incidents—without adding any of the noise. No guesswork. No alert fatigue. Just clean files and confident operations.
The future of cybersecurity isn’t about adding more layers. It’s about making each one count. Try a demo today to see how Votiro can add security layers that matter to your organization.
News you can use
Stay up-to-date on the latest industry news and get all the insights you need to navigate the cybersecurity world like a pro. It's as easy as using that form to the right. No catch. Just click, fill, subscribe, and sit back as the information comes to you.
Sign-up Here!
Subscribe to our newsletter for real-time insights about the cybersecurity industry.



