The High Cost(s) of Security Non-compliance

Many teams treat compliance like an everyday checklist. That is, until they find out the hard way that it’s a security issue, too.
The cost of non-compliance is rarely confined to a line-item fine. The real impact strikes at your ability to operate, compete, and retain customer trust. It’s the kind of failure that doesn’t show up in just a quarterly report. Non-compliance bleeds into every department, drags down growth, and exposes the business to risks that no insurance policy can fully absorb.
Now, to be clear, the point of this blog isn’t to scold. It’s to reframe how we talk about compliance. The objective is to treat it as less of an obligation, and more as a strategic differentiator that secures your business from threats—inside and out.
What Non-Compliance Really Costs Organizations
Fines are the headline. But they’re not the whole story. When a regulator shows up, they’re not just tallying how many controls you failed to meet. Audits uncover weak points in your processes, liabilities in your architecture, and signals that your business isn’t resilient enough to face the threats you claim to mitigate.
The Financial Penalties Add Up Fast
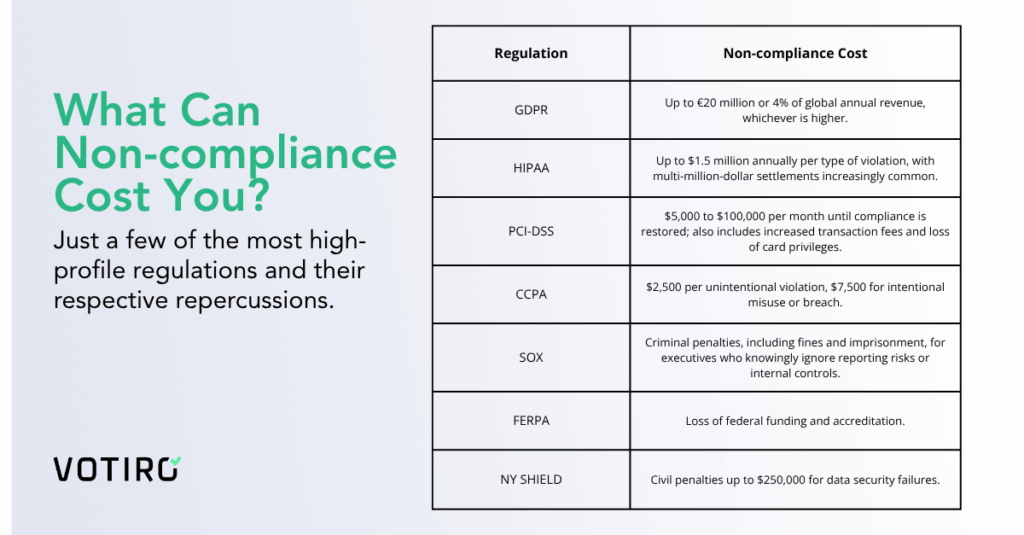
Regulators aren’t handing out warnings; they’re enforcing consequences designed to make companies take notice. These non-compliance fines can equate to:
- GDPR: Up to €20 million or 4% of global annual revenue, whichever is higher.
- HIPAA: Up to $1.5 million annually per type of violation, with multi-million-dollar settlements increasingly common.
- PCI-DSS: $5,000 to $100,000 per month until compliance is restored; also includes increased transaction fees and loss of card privileges.
- CCPA: $2,500 per unintentional violation, $7,500 for intentional misuse or breach.
- SOX: Criminal penalties, including fines and imprisonment, for executives who knowingly ignore reporting risks or internal controls.
- FERPA: Loss of federal funding and accreditation.
- NY SHIELD: Civil penalties up to $250,000 for data security failures.
These aren’t slap-on-the-wrist fines. They’re budget-breaking, brand-damaging, potentially career-ending risks. For mid-market companies, growth-stage tech firms, and even enterprise giants under regulatory scrutiny, non-compliance can quickly shift from a red flag to a red line.
But the Bigger Losses Don’t Come from Fines
You can write a check for the penalty. But you can’t buy back trust from a partner or customer who saw their confidential data leaked because of your sloppy file handling. You can’t re-close a deal that stalled when your vendor security review failed. And you definitely can’t just shrug off federal dis-accreditation.
- Legal claims.
- Class-action lawsuits.
- Lost contracts.
- Skyrocketing cyber insurance premiums.
- Stakeholder skepticism.
These are the operational and reputational shocks that ripple outward from non-compliance incidents. And they don’t fade quickly. A single breach involving poorly handled data can cost years of brand equity, erode your strategic partnerships, and send acquisition talks cold.
Where Non-compliance and Cybersecurity Cross Paths
Security and compliance may start in different lanes, but when files are involved, they converge fast. A missed policy isn’t just a regulatory issue, it’s often a threat vector in disguise. Files that aren’t properly scanned, sanitized, or logged don’t just fail audits, they bypass security controls, carry hidden malware, and expose sensitive data. What looks like a paperwork problem quickly becomes a breach-in-waiting. The truth is, weak file handling undermines both your compliance posture and your threat defense. Ignore one and you compromise the other.
Unscanned Files Are a Quiet Threat to Compliance
Organizations transfer thousands of files per day via email, browser downloads, upload portals, API calls, and shared drives. Most of these files are never fully inspected. That’s not just a threat vector—it’s a compliance time bomb.
- PDFs with embedded scripts.
- Word docs with active macros.
- ZIP files with encrypted payloads.
- Even seemingly innocent images can contain malicious code or exposed PII.
- And because most AV tools and DLP rules either miss these risks or block them too aggressively, users work around them.
Workarounds create shadow workflows. Shadow workflows bypass security tools. By bypassing your security tools, sensitive data ends up being handled in ways your auditors won’t sign off on.
File Visibility Gaps Kill Audit Readiness
What happens when your audit team asks for a complete timeline of how a sensitive file was received, scanned, sanitized, accessed, and stored? You’re not audit-ready if your answer involves digging through three tools and a shared inbox.
A strong compliance posture requires:
- Real-time insight into file transfers.
- Logs that show exactly when threats were neutralized.
- Policy-based enforcement that can be demonstrated on demand.
Without these in place, you’re not just vulnerable, you’re deemed undocumented. And in compliance, no documentation means no defense.

The Business Value of Getting Compliance Right
When done well, compliance delivers far more than regulatory peace of mind. It signals to customers, partners, and regulators that your organization takes security seriously and operates with discipline. That trust becomes a competitive edge, opening doors to new markets, smoothing vendor reviews, and accelerating procurement cycles.
Internally, strong compliance practices improve operational resilience, reduce risk exposure, and even help control insurance premiums. It’s not just a legal obligation, it’s a foundation for sustainable growth and long-term credibility.
When your file-handling practices meet the standards set by regulations like GDPR, HIPAA, or PCI-DSS, you’re doing more than satisfying auditors.
Proper file-handling translates into:
- Fewer breach events.
- Faster incident response.
- Lower costs associated with remediation and recovery.
- Easier renewals and lower rates from cyber insurance providers.

How to Align Compliance and Security at the File Level
Effective compliance starts with rethinking how files are handled. Instead of reacting to issues after they arise, organizations must build prevention into every step of the file flow. That means treating every file as potentially risky, regardless of origin, and applying consistent security and compliance controls from the outset.
Reduce Exposure Time with Proactive File Sanitization
The longer a file sits unexamined, whether in email, a browser cache, or an upload folder, the greater the chance it contains something malicious or non-compliant. Sanitizing files at the moment of entry (not post-delivery) closes that window. Even zero-day threats can be stripped from business-critical files without relying on legacy scanning engines. To proactively sanitize files using zero trust principles, organizations must look to solutions that do it seamlessly.
Build Audit-ready Visibility
Compliance isn’t just about preventing problems, it’s about proving you did. By logging every file action, every masking event, and every threat that was neutralized, your organization can:
- Respond faster to incidents.
- Provide detailed reports to regulators.
- Strengthen your security story in the boardroom.
This is why organizations also need solutions that provide actionable analytics.
Votiro’s Role in a Proactive Compliance Strategy
Votiro’s Advanced CDR and Active Data Masking deliver real-time sanitization and sensitive data protection without breaking the business flow. Files are rebuilt using only known-safe elements, while sensitive content like PII or PHI is automatically masked based on fine-grain policy controls.
- This means securing healthcare data across patient intake systems and insurance exchanges.
- For financial services, it supports compliant handling of payment data, loan records, and transaction files.
- For education, it enables FERPA-aligned exchange of academic records and transcripts.
Votiro’s open-API enables organizations to integrate with their existing email, browser, storage, and collaboration platforms. That means you don’t have to rebuild your stack to achieve continuous compliance enforcement.
Are You Prepared?
- Are your files scanned and sanitized before they reach endpoints?
- Can you automatically mask sensitive data in transit across all channels?
- Do you have centralized logs proving compliant handling of regulated content?
- Can you confidently pass a GDPR, HIPAA, PCI-DSS, SOX, or CCPA audit?
If your answers aren’t airtight, compliance isn’t a guarantee, it’s a gamble. And Votiro can help.

Don’t Let Your Files Be the Reason You Fail the Next Audit
Non-compliance is more than an oversight. It signals to regulators, attackers, and customers that your business hasn’t closed the most important gaps.
Fixing this isn’t about playing defense. It’s about building a business that’s trusted to handle what matters. Try Votiro for free and see how effortless compliance can be before it costs you.
News you can use
Stay up-to-date on the latest industry news and get all the insights you need to navigate the cybersecurity world like a pro. It's as easy as using that form to the right. No catch. Just click, fill, subscribe, and sit back as the information comes to you.
Sign-up Here!
Subscribe to our newsletter for real-time insights about the cybersecurity industry.



