Security Beyond the Perimeter: How DDR Strengthens DLP & DSPM

Security teams invest countless hours fortifying defenses, enforcing policies, and locking down sensitive data, yet breaches still happen. Why? The reality is that traditional security tools like Data Loss Prevention (DLP) and Data Security Posture Management (DSPM) are essential but incomplete. They provide visibility, enforce policies, and attempt to prevent sensitive data from being leaked or misused. However, they don’t actively sanitize threats within files or neutralize sensitive data before it becomes a liability.
DLP vs. DSPM vs. DDR – What’s the Difference?
To really understand why DLP and DSPM are not enough to fully protect sensitive data, it’s important to break down their core functions. DLP acts as a gatekeeper, monitoring and blocking the movement of sensitive data but lacking the ability to sanitize or modify it. DSPM, on the other hand, serves as a visibility tool, identifying where sensitive data resides and flagging potential risks. Yet, it doesn’t take proactive action to secure that data in motion.
While both play crucial roles in data security, neither solution actively neutralizes threats embedded within files or ensures that sensitive data remains protected beyond policy enforcement. This gap leaves organizations vulnerable to sophisticated attacks, accidental data exposure, and compliance risks.
What is DLP? (Inside the Wall)
DLP is like a security checkpoint at the edge of your organization. It monitors, flags, and sometimes blocks sensitive data from leaving. It operates based on predefined policies and classifications, scanning files for information like Social Security numbers, credit card details, or proprietary business documents. If a file matches certain conditions, DLP can block its transmission, encrypt it, or alert security teams.
At its core, DLP is designed to prevent data from escaping your organization, ensuring that confidential information doesn’t end up in unauthorized hands. However, this approach has major limitations:
- All-or-Nothing Approach – DLP is binary in function: it either blocks sensitive data or lets it through. If a file is flagged but critical to business operations, users might bypass the system and send it anyway, undermining security efforts.
- Rigid Policies – DLP systems rely on predefined rules, often leading to high false positives that disrupt workflows. Employees may find themselves unable to send important documents simply because they contain flagged keywords.
- Reactive, Not Proactive – While DLP can stop data from leaving, it doesn’t neutralize threats or sanitize sensitive content. A malicious file entering the system remains just as dangerous, and sensitive data already stored within a document remains intact and accessible.
DLP plays a crucial role in security, but it’s not enough on its own. It focuses on controlling movement rather than eliminating risk.
What is DSPM? (Inside the Wall, But Looking for Cracks)
If DLP is the security checkpoint that prevents data from leaving, then DSPM is the internal auditor constantly checking for weak spots in the walls. DSPM focuses on understanding where sensitive data resides, who has access to it, and whether any configurations or permissions leave it exposed.
DSPM scans cloud environments, databases, and enterprise storage, providing visibility into who has access to what and highlighting potential risks like misconfigured permissions or overly permissive access controls. By identifying where sensitive data is stored and who can access it, DSPM helps organizations understand their risk posture and improve security hygiene.
However, while DSPM provides critical insights, it has key limitations:
- No Protection for Data in Motion – DSPM primarily monitors stored data, meaning it doesn’t actively secure files as they move through emails, cloud applications, or external collaboration tools. Sensitive data could still be intercepted or exfiltrated before security teams notice a problem.
- Identifies Risks, But Doesn’t Fix Them – While DSPM can flag misconfigurations, excessive permissions, and exposure risks, it doesn’t automatically remediate them. Security teams still need to manually address flagged vulnerabilities, which can lead to delays.
- Manual Policy Enforcement – Unlike automated security solutions, DSPM relies on administrators to implement corrections. This often results in gaps between risk identification and resolution, exposing sensitive data longer than necessary.
DSPM is a powerful tool for identifying potential security weaknesses, but it doesn’t neutralize threats or sanitize sensitive data.
Inside the Wall vs. Outside the Wall – The Blind Spot of DLP and DSPM
Security teams rely on DLP and DSPM to keep sensitive data secure. Still, these tools primarily focus on internal environments by monitoring access, enforcing policies, and flagging risks inside the organization’s perimeter. However, the most significant threats often emerge when data moves beyond these controlled environments. Whether through file sharing, email attachments, or third-party collaboration tools, unstructured data is constantly in motion, creating gaps that traditional security tools aren’t designed to address.
Understanding where these solutions fall short requires examining how they operate inside the wall and where they fail to protect what happens outside of it.
Inside the Wall: How DSPM and DLP Handle Data
Within an organization’s security perimeter, DLP and DSPM play essential roles in managing and protecting sensitive data. DLP functions as a guardrail, ensuring that regulated information, like personally identifiable information (PII) or financial records (PCI), doesn’t leave the organization without proper authorization. It enforces strict rules, blocking or flagging data based on predefined policies. Meanwhile, DSPM operates more like a security map, helping organizations identify where sensitive data is stored, who has access to it, and whether it’s at risk due to misconfigurations or excessive permissions.
DLP and DSPM maintain visibility and enforce policy but leave a blind spot when threats bypass initial detection. DLP’s rigid rules often lead to operational bottlenecks or false positives, disrupting workflows. DSPM can expose risky access paths but doesn’t actively remediate them, meaning organizations may still struggle with insider threats, misrouted files, and undetected vulnerabilities. The biggest limitation? Neither solution is designed to neutralize threats before they become a problem. That’s where a proactive approach is needed, protecting unstructured data in motion, inside and outside the organization’s walls.
What is DDR? (Protection Inside and Outside the Wall)
While DLP tries to block sensitive data from leaving and DSPM audits where sensitive data resides, DDR (Data Detection and Response) takes a proactive approach by sanitizing content and obfuscating data before it ever becomes a risk. Instead of relying on predefined rules to allow or block files, DDR removes sensitive elements while keeping files usable, ensuring that security doesn’t come at the cost of productivity.
Unlike DLP, which forces security teams to choose between blocking or allowing data transfers, DDR automatically redacts or masks sensitive data in real-time. This means files can still be shared and used without exposing confidential information. Unlike DSPM, which identifies security gaps but requires manual intervention, DDR actively prevents data leaks before they happen, eliminating the need for reactive remediation.
DDR isn’t just about monitoring data; it ensures that only clean, safe files move in and out of the organization. By combining sensitive data detection with automatic sanitization, DDR closes the gaps left by DLP and DSPM, preventing both accidental and malicious data exposure without disrupting workflows.
Outside the Wall: Protecting What Others Are Missing
While DLP and DSPM provide essential safeguards inside an organization, they fall short when data moves beyond the perimeter. These tools are designed to either block or allow sensitive data, but they don’t sanitize or neutralize threats, leaving organizations vulnerable when files inevitably leave the network.
Cybercriminals have adapted to these limitations, employing zero-day exploits and file-based malware that can slip through detection-based security. Because neither DLP nor DSPM actively cleans the data, sensitive information remains intact within documents, spreadsheets, and PDFs, making it a prime target for attackers if stolen. Even when DLP successfully blocks a file from leaving, the threat within that file is still active, awaiting an opportunity to resurface.
This is where DDR provides a critical advantage. Unlike traditional security tools, DDR doesn’t just monitor or block data. It actively sanitizes it. Before a file leaves or enters an organization, DDR removes sensitive information and eliminates hidden threats, rendering stolen data useless to attackers. This approach ensures that even if cybercriminals breach defenses or exfiltrate files, they walk away empty-handed, providing true data security inside and outside the wall.
How DDR Complements DLP and DSPM
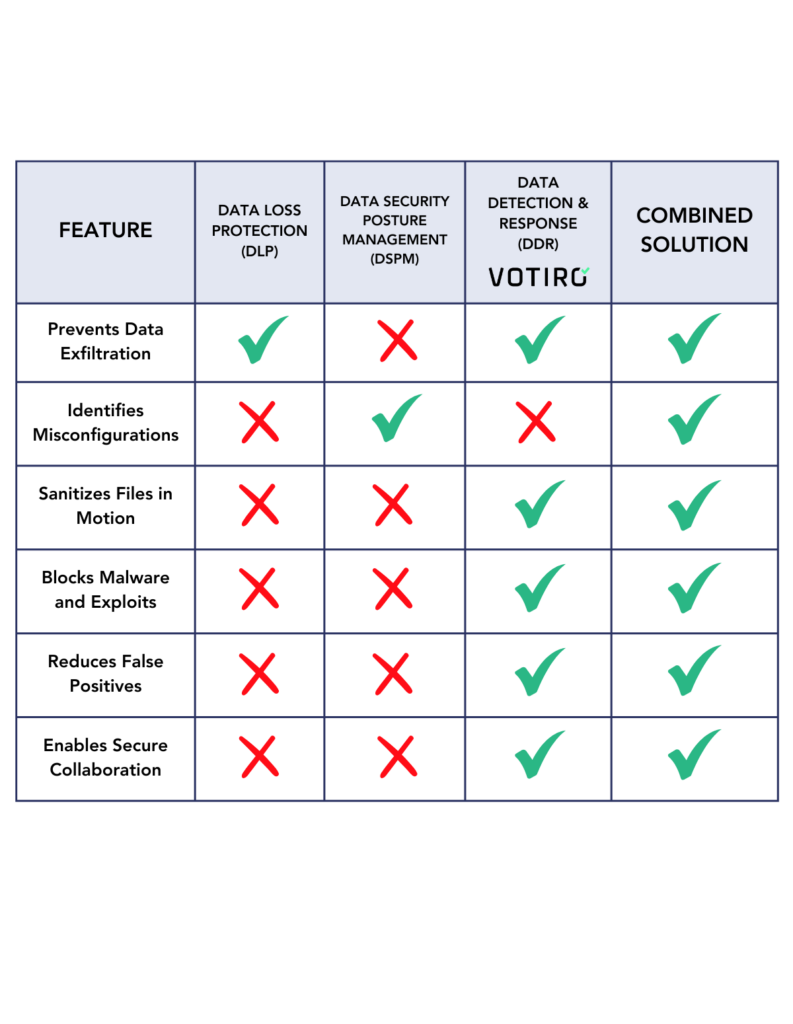
These solutions create a powerful defense to protect your data when used together. DLP prevents exfiltration, DSPM maps risk, and DDR ensures that even if attackers breach your defenses, what they find is unusable.
An Example of Data Security Without DDR
Here’s how a common attack scenario unfolds when an organization lacks DDR:
- An employee downloads a seemingly harmless spreadsheet from an external vendor. The file contains embedded malware but bypasses traditional security checks because it appears legitimate.
- DLP doesn’t block the file because the content doesn’t match a known threat signature. Since DLP primarily focuses on data classification rather than hidden threats, it allows for download.
- DSPM logs the activity but doesn’t intervene. The system notes that a sensitive file has been accessed but doesn’t stop the malware from executing. Its role is visibility, not action.
- The embedded malware executes, establishing a foothold. The attackers now have access to internal systems and can move laterally, searching for valuable data to steal or encrypt.
- Sensitive data has been exfiltrated, and the company is now compromised. DLP and DSPM failed to stop the attack without DDR actively sanitizing the file before downloading it.
This is a fundamental weakness in traditional data security strategies: they focus on controlling data movement but don’t neutralize hidden threats. DDR fills this gap by removing malicious elements from files before they can execute. It ensures that even if a file enters the network, it is clean, safe, and incapable of causing harm.
The Votiro Advantage – Active Neutralization
Instead of relying on detection-based security models, Votiro’s Zero Trust Data Detection and Response proactively removes the threat of malware and masks sensitive data before it can cause harm or be exfiltrated.
With Votiro DDR, every file entering the organization undergoes real-time file sanitization, aka Content Disarm and Reconstruction (CDR), neutralizing hidden malware, embedded scripts, or ransomware before the file reaches secure endpoints. Unlike the aforementioned DLP, which blocks files based on policy-based triggers, and DSPM, which audits data risks without remediation, DDR actively protects files without disrupting workflows.
Delivering a dual-layered defense for organizations, Votiro also takes a proactive approach to data security, for both structured and unstructured data. Even if attackers managed to steal files, they’d receive nothing of value, such as PII, PCI, and PHI. Votiro masks sensitive data based on fine-grained security controls that are unique to each organization, eliminating a key incentive for cybercriminals.
By filling the security gaps and delays left by DLP and DSPM, Votiro provides a missing layer of cybersecurity that doesn’t wait for threats to surface but actively neutralizes them before they can cause harm.
If you are ready to take the next step in securing your data, inside and outside the wall, schedule a demo today and see how easily your organization can get started.
News you can use
Stay up-to-date on the latest industry news and get all the insights you need to navigate the cybersecurity world like a pro. It's as easy as using that form to the right. No catch. Just click, fill, subscribe, and sit back as the information comes to you.
Sign-up Here!
Subscribe to our newsletter for real-time insights about the cybersecurity industry.



