RBI Alone Isn’t Enough – How CDR Closes the File Security Gap
Every business relies on the web in one way or another—whether for communication, collaboration, or accessing essential cloud-based applications. But as essential as the web might be, it’s also one of the most exploited attack vectors for cybercriminals. Malicious actors use sophisticated techniques to turn everyday browsing into a launchpad for cyber threats, embedding malware in seemingly harmless downloads, exploiting vulnerabilities in web applications, and tricking users with phishing sites designed to steal credentials. If you haven’t been the victim of one of these attacks, you probably know someone (or an entire organization) that has.
Despite advancements in cybersecurity, attackers continue to find ways to slip through the cracks left behind by a reliance on reactive solutions. While traditional security tools like antivirus, firewalls, and secure web gateways play an important role, they often fall short against modern threats.
The Growing Threat of Web-Based Attacks
Browser-based attacks have increased significantly, with attackers honing their ability to exploit everyday web activity, transforming simple browsing, document downloads, and email attachments into security liabilities. While phishing remains a dominant threat, the landscape has evolved beyond deceptive login pages. Cybercriminals now leverage sophisticated techniques like drive-by downloads, where malicious scripts execute in the background without user interaction, or weaponized files that appear harmless but deploy malware upon opening. Even something innocuous as an image file can be a carrier for hidden code, using steganography to bypass detection.
To combat the growing threat of web-based attacks, organizations require a proactive, layered defense that doesn’t rely on cleaning up a mess after a breach has begun.
Remote Browser Isolation (RBI) – The First Layer of Defense
Many organizations rely on RBI as a first line of defense to counter risks. This is due to RBI’s ability to create a virtualized browser session, ensuring that web-based threats never directly interact with the user’s device. Instead of executing code locally, RBI streams a safe, rendered version of the web page to the user. This prevents malicious scripts, browser exploits, and drive-by downloads from infecting endpoints. Additionally, phishing attacks become far less effective as users engage with an interactive image of the page rather than the actual malicious site.
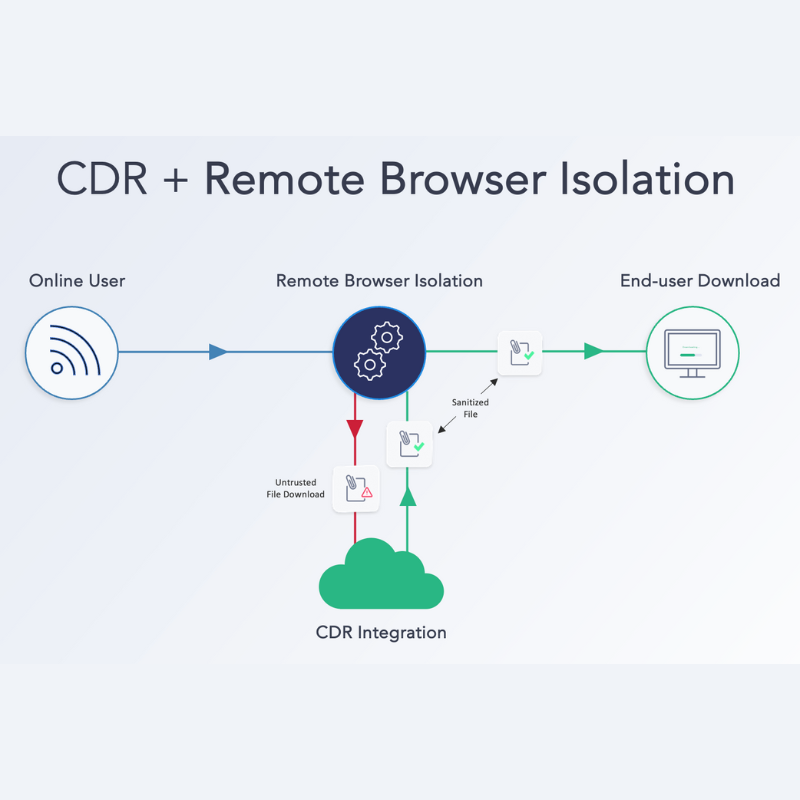
Pairing RBI with a tool like Content Disarm and Reconstruction (CDR) creates a seamless, proactive security framework that ensures no threats make it through. While RBI isolates the browser and prevents immediate execution of malicious scripts, it doesn’t stop users from downloading infected files. With CDR, however, any file that bypasses RBI’s protections is automatically sanitized before it reaches the user, eliminating hidden dangers.
Moreover, RBI is limited to active browser sessions—it doesn’t address threats introduced through email attachments, cloud file transfers, or other sources. That’s where CDR technology comes into play, filling the security gap by ensuring that any file entering the organization is sanitized and threat-free before it can be opened or shared.
CDR – The Missing Layer in File Security
Unlike traditional antivirus or sandboxing solutions that rely on detection, Content Disarm and Reconstruction doesn’t need to recognize a threat to eliminate it. Instead, it deconstructs every file, removes potentially harmful elements like embedded scripts, macros, or malware payloads, and reconstructs a clean, fully functional version.
Here’s a simplified look at how the CDR process works:
The Key Benefits of a CDR + RBI Strategy
With CDR + RBI, businesses no longer have to choose between security and usability. Employees can browse freely, download files safely, and collaborate without fear of hidden malware or accidental data leaks.
- Prevents Malware Infections—This approach removes the attacker’s entry points by isolating browser-based threats and sanitizing downloaded files, preventing malware from taking hold.
- Reduces False Positives—Traditional security tools, such as DLP, often block legitimate content, frustrating users and slowing productivity. CDR ensures that users receive their files in a safe, threat-free format.
- Stops Both Web-Based and File-Based Threats—Attackers don’t rely on a single method, nor should your security. This layered defense eliminates threats, whether they attempt to enter via a browser session, file download, email attachment, or cloud storage.
Why Votiro CDR + RBI is the Future of Web and File Security
Cyber threats are evolving faster than ever, exploiting every possible entry point to infiltrate organizations. Relying on a single security tool is no longer enough—attackers constantly adapt, bypassing traditional defenses and making headlines in the process. To stay ahead, businesses need a proactive, layered approach that eliminates threats before they can cause harm.
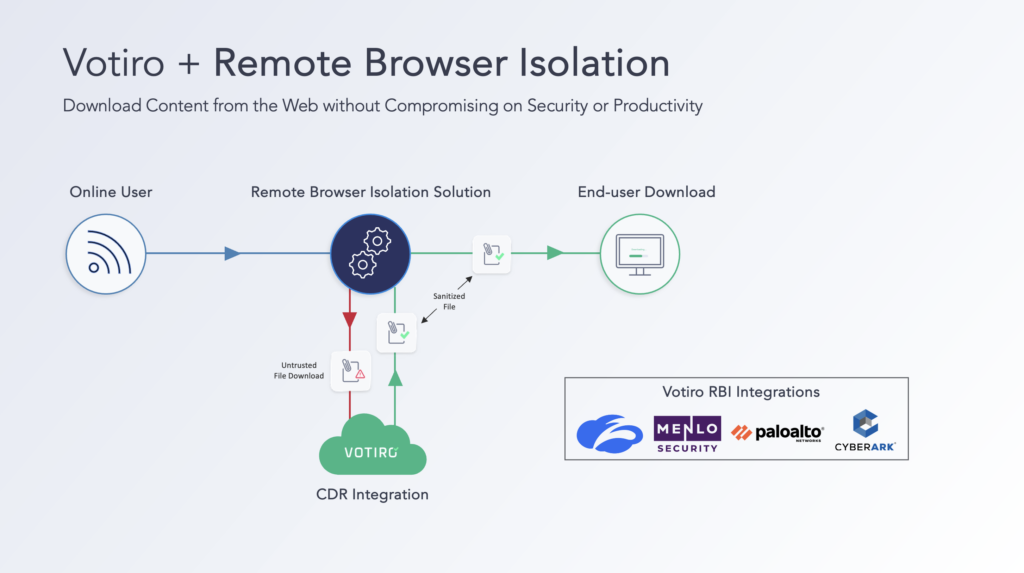
By using Votiro’s advanced CDR and pairing it with an RBI solution, businesses no longer have to choose between security and usability. By combining these two technologies, organizations gain a frictionless security model that protects against evolving cyber threats while maintaining productivity.
In addition to CDR, Votiro users have an edge when it comes to their data security. As a Zero Trust Data Detection and Response platform, Votiro provides Active Data Masking, working simultaneously with CDR to discover, identify, and obfuscate sensitive information (PCI, PHI, PII) in motion.
- Eliminates Sensitive Data Exposure—Mask confidential data, prevent accidental leaks, and ensure compliance with data privacy regulations. This means that if files should end up in the wrong hands, the data stored within is all but worthless for exploitation and ransom.
Discover how Votiro’s CDR + RBI can eliminate hidden threats, streamline your security stack, and protect your workforce—without compromise. Schedule a demo today and take the first step toward a secure, seamless browser experience.
News you can use
Stay up-to-date on the latest industry news and get all the insights you need to navigate the cybersecurity world like a pro. It's as easy as using that form to the right. No catch. Just click, fill, subscribe, and sit back as the information comes to you.
Sign-up Here!
Subscribe to our newsletter for real-time insights about the cybersecurity industry.



