DICOM File Security: How Malware Hides Behind HIPAA-Protected Images

What are DICOM files?
A DICOM file is an image from a medical scan saved in the Digital Imaging and Communications in Medicine (DICOM) format. DICOM is the international 30-year-old standard protocol for managing and transmitting medical images, such as ultrasounds, MRIs, X-rays, and CT scans. In addition, these files often include the patient’s identification data, including name, age, date of birth, height, weight, and medical condition. DICOM files facilitate the digital transfer of these images and related data between healthcare entities, eliminating the need for physical films and avoiding compatibility issues.
In 2016, the Box DICOM Viewer – a cloud-based solution designed to enable storing, sharing and viewing any DICOM file on a browser or mobile device – was approved as a class II medical device by the Food and Drug Administration (FDA). As a class II device, medical professionals can use the Box DICOM Viewer for diagnostic purposes. FDA approval was granted after a three-year process during which Box had to demonstrate that through the entire process of uploading, storing, sharing, accessing, viewing, and downloading a DICOM file, there would be no loss of fidelity in the images. Unfortunately, securing these files was not part of the consideration.
How is a DICOM file constructed?
Every DICOM file contains a Preamble, a 128-byte section at the beginning of the file that enables compatibility with image viewers that cannot read DICOM but support other web image formats, such as JPG, PNG, or TIFF. There are no limitations for the data that can be inserted into a DICOM file’s Preamble; as long as the sequence is less than 128 or bytes, it can be inserted in full conformance with the DICOM standard.
How can DICOM files be weaponized?
DICOM files are large due to the amount of data they contain. They are similar to an archival file, functioning as a file that includes other files, providing plenty of space for attackers to hide a malicious element within – a process made even easier by DICOM ports mistakenly exposed on the internet. These can be found using Shodan, a search engine for internet-connected devices that is often used by hackers to locate vulnerabilities.
By altering the Preamble, hackers can trick these image viewers into reading a DICOM file as if it is one of their supported formats—such as an executable–enabling a healthcare staff member to view the image file using their phone or tablet’s image viewer. Alternatively, the attacker can hide a fully-functioning executable within the Preamble, enabling malware to hide behind HIPAA-compliant images. This way, instead of having a DICOM file hidden in another image format, an executable is hidden in a DICOM file.
In both cases, the original patient health information (PHI) image’s metadata is maintained. The malicious file extension is hidden, meaning that the average healthcare worker would never notice anything was amiss as they viewed and transferred the malicious file between departments and other entities, such as health insurance companies.
In addition, because of HIPAA regulations, most antivirus/anti-malware solutions are configured to disregard files that contain PHI. Even if the malware were detected, security teams would be unable to simply delete the file because it contains the HIPAA-protected—and important—PHI. According to the researcher who discovered it, the DICOM malware bug is “the first vulnerability whose technical potency is derived from a regulatory environment in addition to a software design flaw.”
There is no simple fix or patch for this flaw, and imposing new standards for the DICOM’s Preamble while maintaining its widespread compatibility, is a significant industry challenge.
The outcome of a DICOM malware infection
The centrality of DICOM files to the healthcare system allows hackers broad access to spread the malware’s payloads beyond the hospital’s clinical devices and internal network into the wider healthcare network, as routine workflow sees these files transferred to other practitioners, facilities, and institutions.
These compromised DICOM files can result in:
- Disruption of operations
- Unauthorized access to sensitive medical information
- Unauthorized access to system resources
- Noncompliance with medical guidelines/regulatory fines for HIPAA violations
- Malicious manipulation of medical images
- Class action lawsuit costs
- Damage awards and settlements
- Serious reputational damage
- Expensive recovery efforts
Example of a malware infection via DICOM security
In one scenario, a hacker inserts malicious code in a DICOM file and emails it to a doctor’s office, in the form of a phishing email. The unsuspecting office staff opens the DICOM file, unleashing the malware onto the office network and corrupting other DICOM files while evading detection. As this physician regularly refers patients to the local hospital, the infected DICOM files are unknowingly emailed to the hospital, spreading the malware to the hospital’s network and causing further damage.
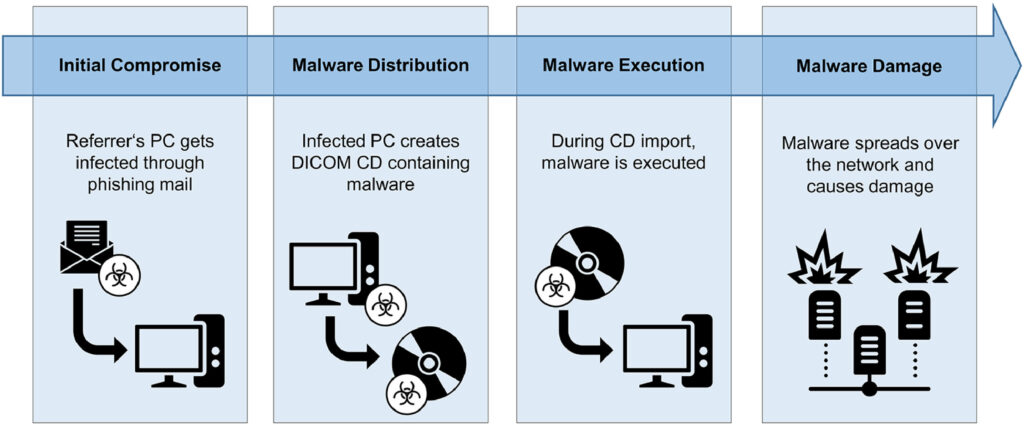
Attack-ready DICOM malware
There are a number of examples of security breaches and malware attacks via DICOM files. Here are a few:
- In 2017, researchers uncovered 2,782 unprotected DICOM servers worldwide, with the majority located in the United States.
- In 2019, a researcher used the Internet scanning tool Shodan to uncover more than 1,100 DICOM unprotected servers, mostly in the United States. As proof of his ability to access and retrieve DICOM images, he printed a 3D model of a patient’s pelvis.
- In March 2019, a security researcher used deep learning to alter CT and MRI scans in DICOM files during the transfer from scanner to PACS, evading the notice of 99% of radiologists who reviewed the converted images.
- In April 2019, a researcher hid malware in DICOM files, effectively evaded detection until the malware was activated and compromised the computer system.
Healthcare experiences threats through DICOM files
The healthcare sector is becoming an increasingly attractive target by cyber-attackers. The underlying problem with file-borne threats facing health organizations in the healthcare system lies with both human error from people working within the system and with the devices and digital technologies such as the Box DICOM Viewer that are helping to modernize healthcare by increasing file accessibility and interoperability. While DICOM malware files represent an immediate threat to healthcare organizations, there are many other threats as well, behooving the industry to practice proactive cybersecurity and actively defend themselves against all forms of attacks.
How to prevent DICOM malware
Weaponized files are an issue for all industries dealing with documents and documentation, but healthcare and healthcare insurance is especially at risk. Today, a new technology that eliminates file-borne threats while preserving file functionality and usability is helping healthcare organizations around the globe to significantly reduce their risk while preserving workflows and the free–and critical–transmission of data.
News you can use
Stay up-to-date on the latest industry news and get all the insights you need to navigate the cybersecurity world like a pro. It's as easy as using that form to the right. No catch. Just click, fill, subscribe, and sit back as the information comes to you.
Sign-up Here!
Subscribe to our newsletter for real-time insights about the cybersecurity industry.



