Cybersecurity Insights: Enhancing Control Adoption and Efficacy

Traditional security methods often require users to engage with prompts, follow complex protocols, and maintain heightened awareness—all of which lead to fatigue and, ultimately, a breakdown of inconsistent security practices. With the rapid pace of business, security can become a barrier rather than a safeguard, prompting users to skip steps or ignore protocols to avoid workflow disruptions. This reliance on user participation creates gaps that attackers can exploit, undermining the very purpose of security controls.
Fortunately, there are security options that no longer solely rely on people to ensure security happens. In this article, we explore in-depth the challenges of manual security efforts and provide ways security can operate seamlessly behind the scenes, empowering users to focus on their work and trusting that security is actively managing potential threats without relying on their constant attention.
Cybersecurity Inefficiency: High-Level Problems with a Lack of Human-Centric Design
Digital security controls that depend on user action often lead to inconsistent application, productivity challenges, and heightened risk. Each manual interaction creates opportunities for error, whether from oversight or inconsistency, introducing security gaps that compromise reliability. When employees are frequently required to engage with security controls, operational friction can develop, interrupting workflows and reducing productivity. However, these gaps affect more than security, with data compliance risks increasing as security effectiveness relies on individual participation.
Issue: Increased Risk Due to Human Dependency
When security controls depend on human action, there is an inherent risk that critical steps may be missed or improperly executed, resulting in vulnerabilities that malicious actors can exploit. Unlike automated systems, human intervention is prone to inconsistency, allowing for errors that may bypass even the most rigorous security protocols. In such a system, users might skip or ignore necessary security steps, either by accident or due to task fatigue, leaving openings that could be targeted by attackers. Lack of automation also leads to significant delays in threat mitigation, with hours of unimpeded infiltration causing incalculable damage in the form of government fines, ransomware payments, and consumer reputation.
Additionally, insider threats—whether from negligence or intentional harm—pose a greater risk in environments where security relies on user compliance. The variability in human behavior introduces uncontrollable factors, making security protocols less reliable and creating exploitable gaps that can undermine overall organizational security.
Issue: Operational Inefficiencies and User Frustration
Frequent, repetitive security prompts not only disrupt workflows but also contribute to a sense of fatigue among users. Each required action breaks focus and slows productivity, creating friction that can accumulate over time. When users encounter these repeated interruptions, the time lost to navigating security tasks can detract from their overall effectiveness and morale, leading to operational delays that affect the entire organization.
This constant interruption can also lead to frustration, tempting users to bypass or ignore security controls altogether. A workforce frustrated by excessive security prompts may view them as obstacles rather than safeguards, increasing the likelihood that they will avoid or skip steps meant to protect the organization. Over time, this behavior compounds risk, as bypassed controls create vulnerabilities that compromise security and operational continuity.
Issue: Limited Visibility and Missed Threats
When security controls rely heavily on human awareness, threat visibility is inherently limited. Many risks go undetected due to users’ inability to consistently identify or report them. While security awareness training improves recognition, it cannot provide consistent threat detection in a dynamic threat landscape. Users may overlook or fail to report potential threats, creating blind spots in security coverage.
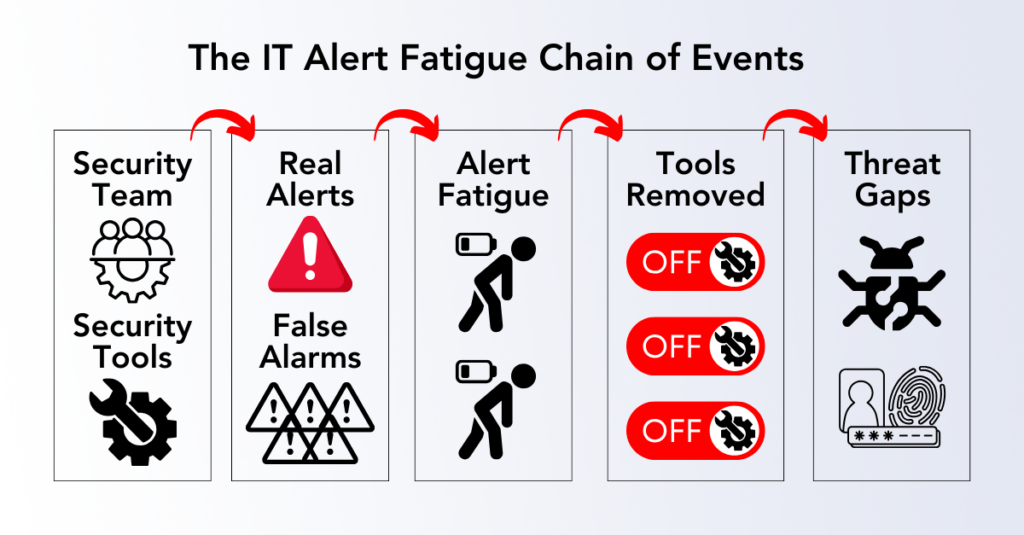
Benefits of a Human-Centric Design for Data Security
A human-centric security design automates critical functions like threat detection and privacy protection, reducing operational friction while maintaining a secure environment. By automatically neutralizing threats in the background, security is enhanced without disrupting daily workflows, creating an effortless experience that encourages widespread security adoption. When data security solutions employ a Zero Trust model, such a design treats all files as potential risks, strengthening defense without added user input. Additionally, a proactive, privacy-focused approach supports compliance, safeguarding sensitive data with minimal friction.
Benefit: Real-Time, Automated Threat Removal
Automated threat removal ensures that files remain secure by identifying and neutralizing hidden malware in real-time without user involvement. This proactive approach eliminates embedded threats in files shared across various channels—whether through emails, uploads, or downloads. Automated threat detection and disarmament tools, such as content disarm and reconstruction (CDR), can maintain file integrity and security by operating seamlessly in the background, allowing workflows to continue uninterrupted. This proactive removal of malware, ransomware, and other threat varieties leads to less risk of sensitive data exposure and resultant data breaches.
Removing the need for 24/7 manual threat analysis from routine processes enables efficient team collaboration. Users can share and receive files without the burden of assessing risk in each interaction, minimizing the potential for file-borne attacks. This proactive disarmament strategy reduces the risk of infection and bolsters productivity, as security measures no longer slow down essential tasks—both for IT and end-users.
Benefit: Privacy Protection Through Zero Trust Framework
A Zero Trust framework enhances privacy by scrutinizing every file, regardless of its source, before it enters the organization. Treating each file as a potential risk ensures sensitive information is secured without user oversight. Automated data masking further strengthens compliance with privacy regulations, maintaining user privacy while allowing seamless file sharing across platforms.
This high level of automated scrutiny mitigates the risk of data exposure by securing files preemptively, reducing potential liability for organizations. Protecting files before they are accessible within the company limits vulnerabilities and upholds privacy standards, all while allowing users to collaborate effectively. Through these background privacy protections, organizations can confidently share information without compromising security or regulatory compliance.
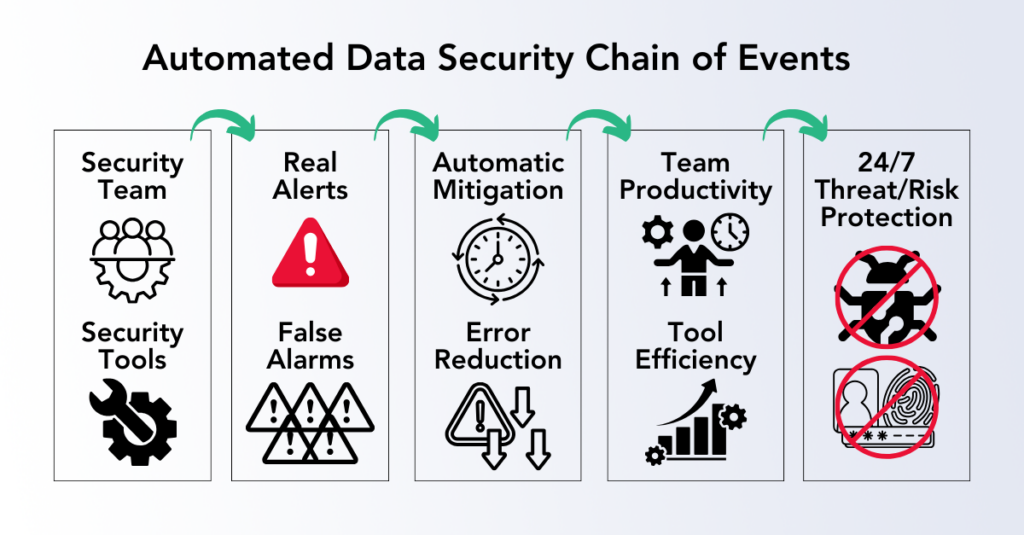
How Votiro’s Zero Trust Data Detection and Response Enables Security Efficiency
Votiro’s advanced Data Detection and Response (DDR) platform can help your organization streamline data security. Using a Zero Trust approach, data flows are monitored in real-time to protect sensitive information without the need for manual intervention. This strategy ensures that personally identifiable information (PII) (as well as PCI and PHI) is promptly recognized and classified before and after it circulates within an organization. Automated protocols manage and safeguard this data, ensuring it complies with business and regulatory standards. This active management mitigates the risk of unauthorized access, providing a solid line of defense against potential data breaches.
Our DDR platform goes beyond traditional firewalls and legacy security measures, safeguarding data privacy by integrating proactive solutions to neutralize malicious threats that cross organizational boundaries. Our patented Content Disarm and Reconstruction technology works as a foundational measure of our DDR solution, automatically sanitizing files as they flow through. It works alongside integrated antivirus (AV) capabilities to proactively address known and emerging zero-day threats, enhancing security and privacy. This enables files to come out safe to use, without users ever being aware of the security happening behind the scenes.
You can learn more about Votiro’s Zero Trust Data Detection and Response capabilities by signing up for a one-on-one demo of the platform. If you’re ready to prevent malware and protect the privacy of your data, you can also try our platform free for 30 days.
News you can use
Stay up-to-date on the latest industry news and get all the insights you need to navigate the cybersecurity world like a pro. It's as easy as using that form to the right. No catch. Just click, fill, subscribe, and sit back as the information comes to you.
Sign-up Here!
Subscribe to our newsletter for real-time insights about the cybersecurity industry.



