Adding File Security to Your Email Platform

By John Masserini, Senior Research Analyst, TAG Cyber
Since 2018, the user base of Microsoft Office 365 has steadily grown from 155 million to more than 345 million in 2022. Unlike Google’s Workspace, whose growth was predicated by a free email platform, Microsoft’s growth is founded in the migration of large-scale enterprises moving from legacy on-premise Exchange environments to a cloud-based, O365 experience.
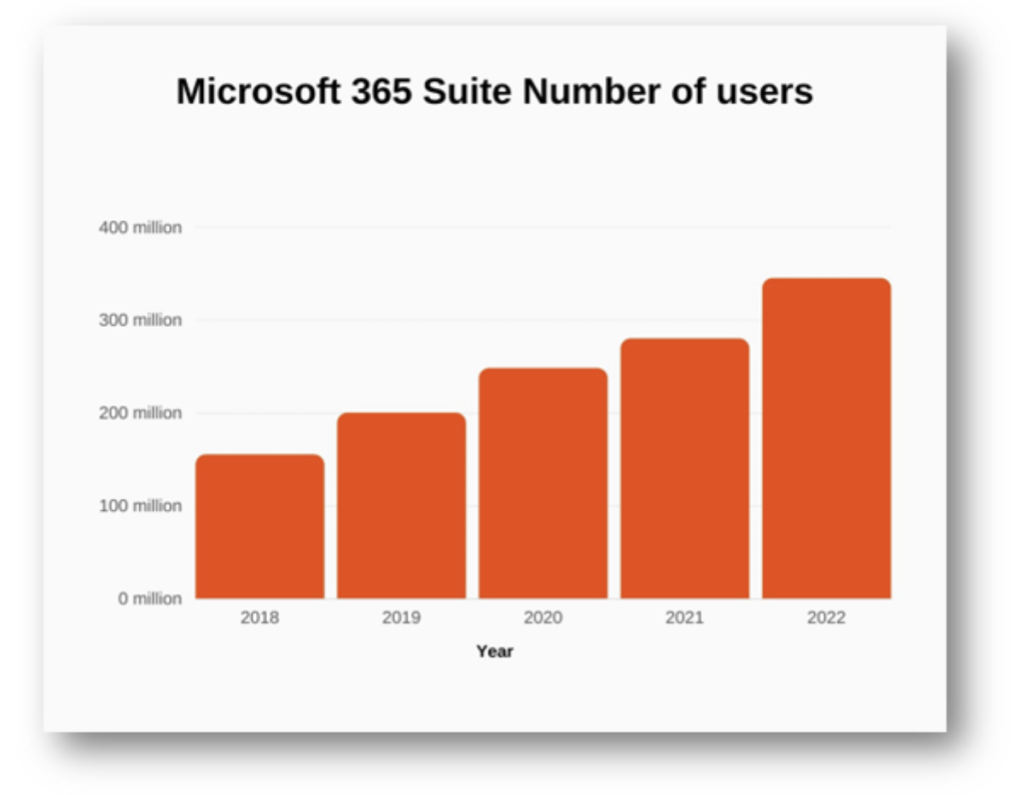
Figure 1: O365 User growth 2018-2022, SignHouse
As these enterprises rationalize their new SaaS experiences, they have quickly realized that many of the controls they had previously relied on are no longer valid. Secure Email Gateways, antivirus scanning, and email sandboxing, the stalwarts of email security controls, were rendered useless in the new cloud model.
The New Collaboration Model
As more organizations move towards SaaS-based collaboration platforms, the risk of the introduction of malware-laced files into the collaboration channel is rapidly increasing. No longer can security teams rely on inline devices, passive scans, or other legacy alternative solutions to protect enterprise communications.
Without question, one of the most challenging aspects of protecting an enterprise today is the amount of unstructured data that is shared amongst employees, business partners, third parties, and customers. As these SaaS collaboration tools become more ubiquitous, documents, spreadsheets, PDFs, and presentations all move in and out of the enterprise with barely a second glance. Not only do they traverse the collaboration platforms continually, but they are also read and modified on countless types of devices with unknown provenance. The reality is, an enterprise has absolutely no understanding of where a document has been, who has modified it, and, worst of all, what’s contained within it.
For the last several decades though, many enterprises have relied upon ‘sandboxing’ techniques to capture and detonate potentially malicious file attachments within emails, network, and web gateways. While these solutions were fairly effective in the beginning, it did not take long for attackers to figure out how to slip past them, either through timed detonation, virtual environment detection, encrypting and password-protecting files, or simply waiting for other events to trigger them. While there are many modern sandboxing solutions in the market today, they generally all fall victim to a determined attacker who is trying to avoid them.
The Call for CDR
Today’s enterprise needs a solution that is not only far more effective but also covers the multitude of an organization’s communication channels – not just email. This is where a modern content disarm and reconstruction (CDR) solution shines its brightest. Where Secure Email Gateways, Exchange anti-virus scanners, and sandboxes all focused on email, modern enterprises leverage everything from Office365 and Google Workplace, to Slack, Zendesk, SalesForce, and Box – along with dozens of other collaboration platforms, all capable of transferring unstructured data files in and out of your company.
Unlike the legacy approach of searching for malicious objects within files and removing them, CDR solutions extract the known good from a file and rebuild that file with those known good components from a standard, trusted template, providing complete document functionality with none of the embedded malicious objects that could detonate at any time. Contrary to many of the legacy, scanner-based tools in use now, this functionality works across all modern, API-capable collaboration channels, regardless of how the file is transferred. It is safe to say that a preponderance of corporate business is now performed over Slack, MS Teams, or Google Chat, and ignoring that channel in your data security program can cause a significant impact on your content security strategy.
Additionally, a CDR solution can also empower your internal business process by enabling customer self-service by facilitating customer uploads of financial documents, healthcare records, or any other kind of document needed – all while knowing the documents will be completely safe and sanitized by the time the employees review them or the automated workflow ingests them. Gone are the days of subversive malware bringing your automation workflows to a grinding halt.
As the enterprise continues leveraging alternate, SaaS-based collaboration solutions, it must also rethink its risk mitigation and overall communications strategy. The adoption of modern collaboration platforms will not just continue but increase over the coming years, so security teams must have a strategy in place to support this fundamental shift. Integrating SaaS solutions with a cloud-based CDR platform is paramount to ensuring that documents and unstructured data are shared in a way that securely aligns with modern business processes.
News you can use
Stay up-to-date on the latest industry news and get all the insights you need to navigate the cybersecurity world like a pro. It's as easy as using that form to the right. No catch. Just click, fill, subscribe, and sit back as the information comes to you.
Sign-up Here!
Subscribe to our newsletter for real-time insights about the cybersecurity industry.



