2023 Verizon DBIR Takeaways: 9 Ways Hackers Use Files to Attack Organizations

The annual Verizon Data Breach Investigations Report (DBIR) is an essential resource used by enterprise security leaders to understand the latest trends in cybersecurity and learn lessons on improving organizational defenses. Let’s review some of the key highlights and see how Votiro can address and mitigate many of the most pressing security issues resulting in a breach.
Key Learning #1: System intrusion has doubled as an attack vector
System intrusion refers to complex attacks that use malware and other hacking techniques where an intruder gains unauthorized access to a system. 97% of the time, system intrusions are executed for financial gain. System intrusion has doubled as an attack vector in 2023, with ransomware dominating as the favorite of threat actors for confirmed breaches.
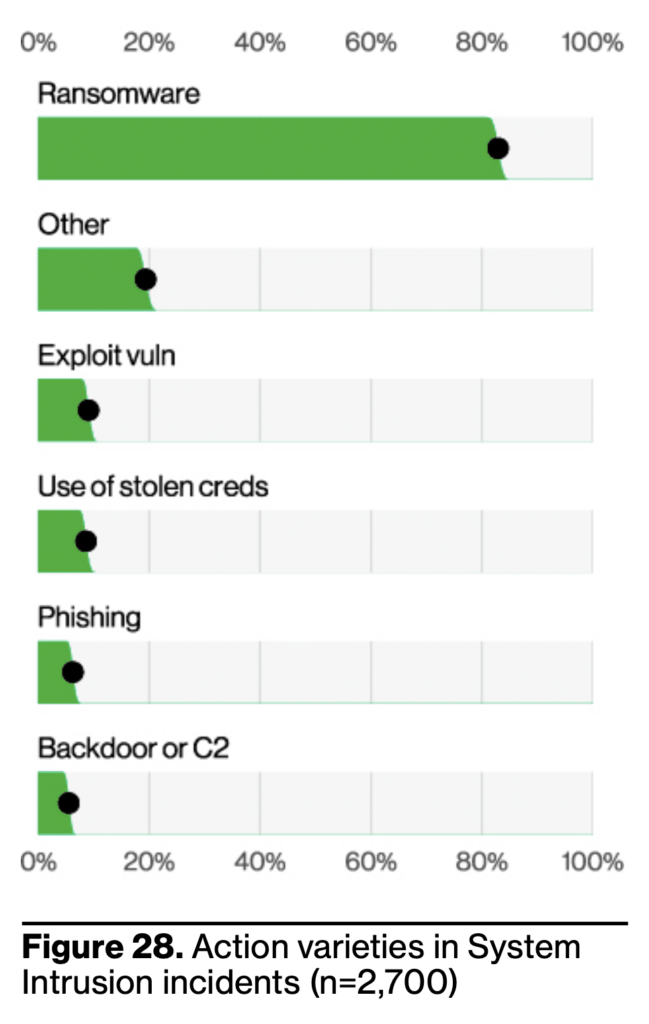
How Votiro can help: Preventing malware from landing on the endpoint is key to preventing system intrusion. Votiro’s innovative Zero Trust approach to file security removes all possible threats without requiring anyone to search for them. Unlike detection-based file security solutions that scan for suspicious elements and block some malicious files, Votiro’s technology singles out only the safe elements of each file, ensuring every file that enters your organization is safe. Keeping malware out in the first place is the best defense you can take to stop system intrusion from wreaking havoc on your organization.
Key Learning #2: Email-based malware remains a favorite
Sending weaponized files directly to user devices is an oldie-but-goodie, and still being used regularly by threat actors looking for an easy way into an organization. Email continues to be the most commonly-used delivery method to distribute malware. That’s because hackers are still finding success using a basic email. Despite awareness campaigns, the median fail rates for attachment and link campaigns are still 4% and 4.7% respectively. The malware is often hidden in productivity files like Microsoft Office documents, as these file types do not arouse suspicion and now have the ability to run code on the user’s system.
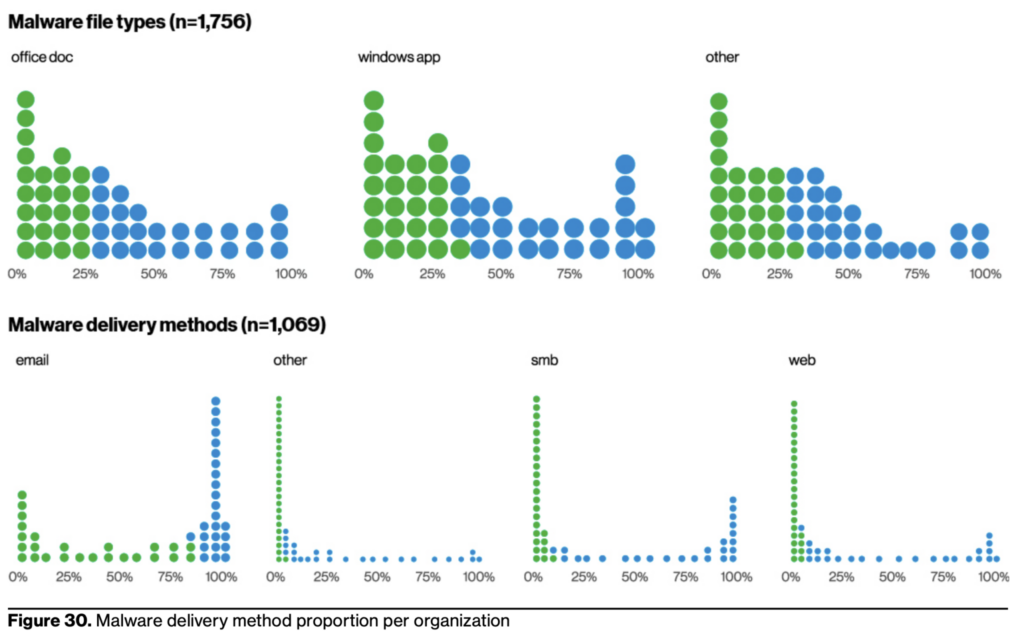
How Votiro can help: No matter which delivery method an attacker chooses, Votiro’s technology keeps an organization safe from file-based malware. That’s because Votiro trusts no unknown, suspicious, or malformed elements of content, proactively removing them before passing on only the good elements of files. Active code and benign macros are kept, and, through the file sanitization process, only the malicious elements are removed. Votiro protects against 180+ weaponized file types, including Microsoft Office documents, pdfs, and image files, all the way to more complex formats like archives, zipped, and password-protected files.
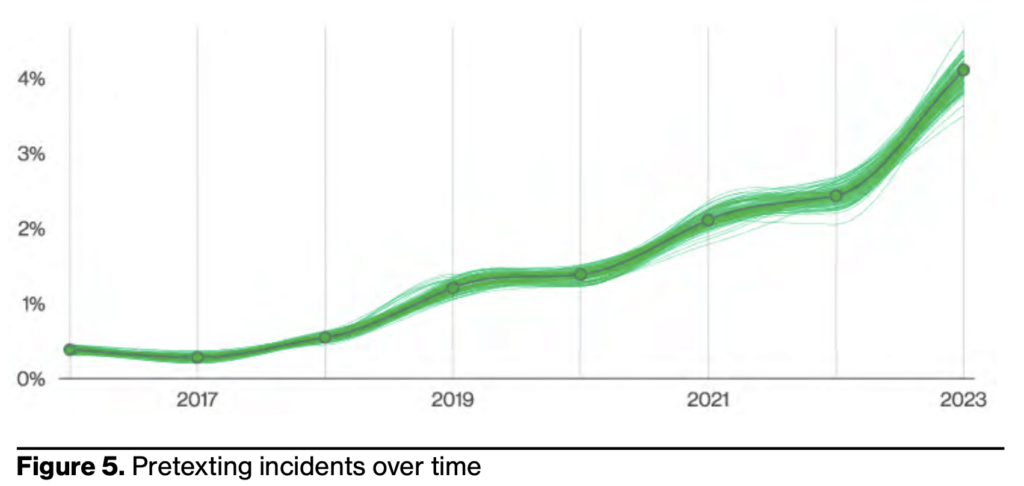
Key Learning #3: Business Email Compromise make up 50% of all social engineering attacks
Business Email Compromise (BEC) is a type of cybercrime that involves unauthorized access to email accounts for financial gain. Also known as “CEO fraud,” BEC attacks typically target businesses, government organizations, or individuals who perform financial transactions via email. In a typical BEC attack, cybercriminals employ various tactics to deceive the targeted individuals or organizations, such as impersonation and social engineering techniques to gain the victim’s trust. According to the Verizon report, Business Email Compromise attacks (which are in essence pretexting attacks) have doubled in the past year and now represent 50% of all social engineering attacks.
“Social Engineering attacks are often very effective and extremely lucrative for cybercriminals. Perhaps this is why Business Email Compromise (BEC) attacks (which are in essence pretexting attacks) have almost doubled across our entire incident dataset, as can be seen in Figure 5, and now represent more than 50% of incidents within the Social Engineering pattern.”
– Verizon DBIR 2023
How Votiro can help: Securing email attachments and content is vital in addressing many email attack vectors. While updating security software and investing in employee education is paramount, having a higher degree of email protection is key to protecting against sophisticated BEC attacks. Votiro singles out only the elements of emails and attachment content known to be fully secure. This enables employees to open emails and file attachments with peace of mind and without any delays or disruptions to business.
Key Learning #4: Ransomware involved in 24% of all breaches
Ransomware is a form of malware that encrypts or locks down the files and data on a victim’s computer or network. The attackers behind ransomware demand a ransom payment from the victim in exchange for decrypting the files and restoring access. The technique remains a popular one, with 24% of breaches across all organization sizes involving ransomware.
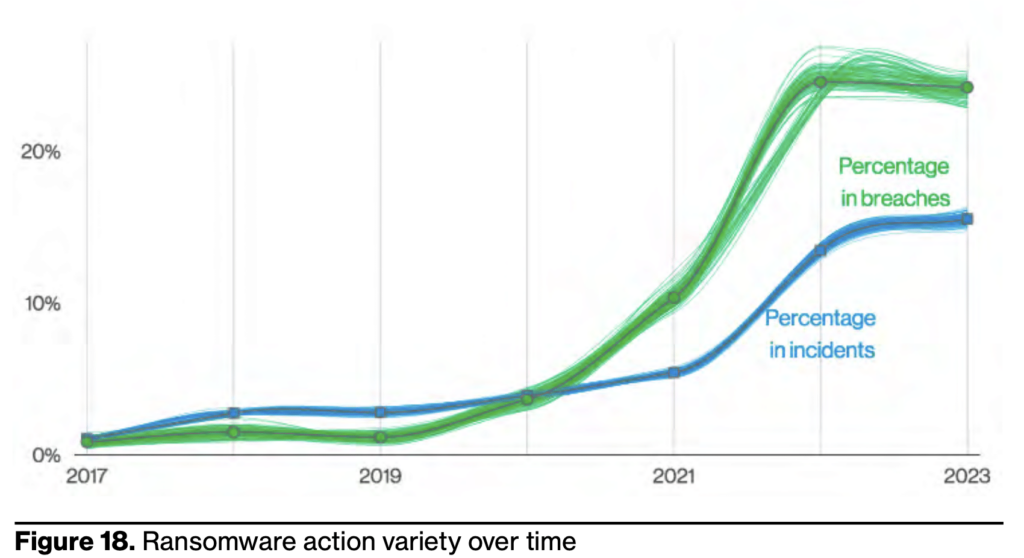
Hackers distribute ransomware in multiple ways. The number one distribution method is Email, as it is both timeless and convenient, with desktop sharing software and Web applications rounding out the top three.
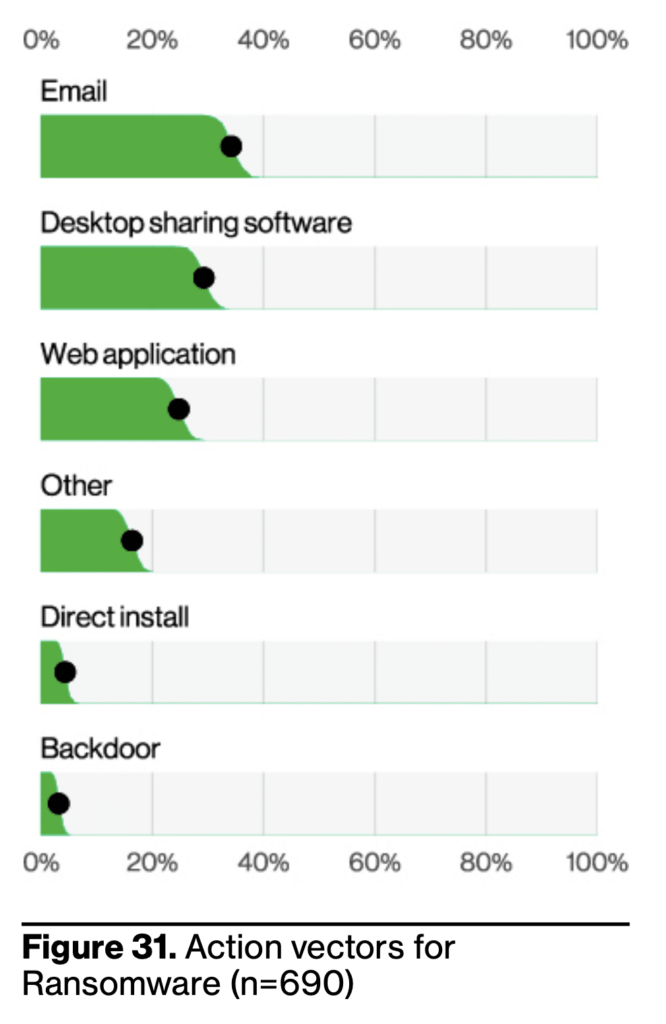
How Votiro can help: Prevention, preparation, and a proactive cybersecurity approach are key to mitigating the risks associated with ransomware attacks. As ransomware software can enter through many content entry points, employing Votiro’s technology cloud to secure the organization’s entry points is an effective safeguard against ransomware threats.
Key Learning #5: Log4j appeared in 8% of organizations
Log4j is an open-source Java-based utility maintained by Apache, commonly used to log security and performance information in a range of consumer and enterprise services, websites, and applications. Remote threat actors have learned to exploit any Log4j vulnerabilities to take control of an affected system. The Log4Shell exploits can be delivered via malicious documents sent via phishing emails and uploaded into customer- or public-facing portals and applications. They are so stealthy that the Verizon report found that Log4j vulnerabilities showed up in 8% of organizations, and 22% of these organizations had multiple instances of the vulnerability detected in their systems.
Watch this video to see how the Log4j exploit is delivered.
How Votiro can help: With Votiro, even unknown and zero-day malware are proactively sanitized, preventing threats from infiltrating the organization. While the Log4j exploit is wide-reaching, Votiro can help protect against any vulnerabilities delivered via documents.
Key Learning #6: Human Error involved in 74% of breaches
Human errors contribute significantly to many data breaches and security incidents. Despite advancements in technology and security measures, humans remain susceptible to mistakes, negligence, and social engineering tactics. In fact, 74% of all breaches include the human element, with people falling victim to phishing and Social Engineering attacks by clicking on malicious links, downloading infected attachments, providing login credentials to attackers, or using weak passwords that are easily breached.
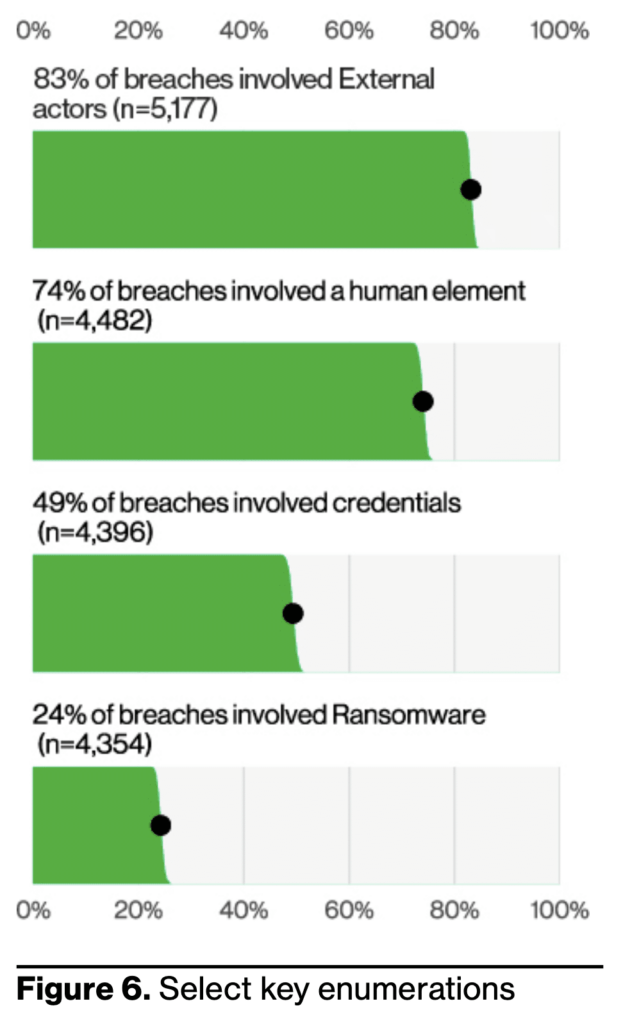
How Votiro can help: Humans will always be the weakest link in any organization and the ones most likely to open or download a weaponized file. Implementing technology, such as Votiro, that does not rely on human detection and instead allows employees to safely open any file is key to preventing malware entry and safeguarding the organization.
Key Learning #7: Healthcare is a target
Healthcare continues to be a significant target of hackers due to the lucrative market for financial and medical data. Digital accessibility has improved services but also increased cyber-attack risks. HIPAA privacy rules aim to protect medical information, but the issue lies in files transferred via insecure sources like email. The high volume of files poses a greater risk of clicking on malicious attachments, granting hackers access to sensitive information. Current security systems fall short of safeguarding complex interactions among health insurance companies, medical institutions, and customers. Exploiting human error and data sources, hackers inject weaponized files into networks, evading security infrastructure.
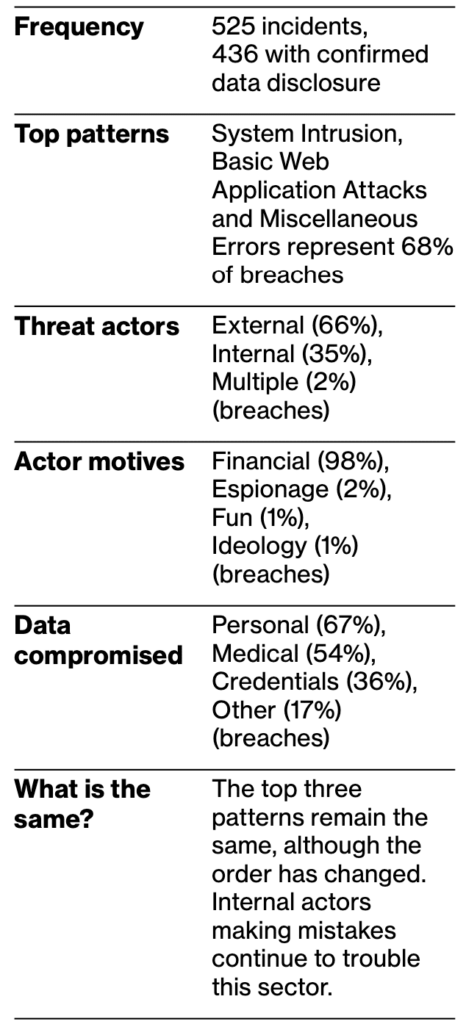
How Votiro can help: Votiro’s technology offers 100% protection against weaponized files aimed at healthcare organizations and health insurance companies. Votiro ensures that all digital transfers and files, including images from medical scans and patient health information saved in DICOM files, are free of malicious elements. Votiro allows you to open any file with no fear of file-based attack, enabling the healthcare industry to safely receive and view files from any channel, effectively protecting against any type of file-based malicious content.
Key Learning #8: New Verticals are being targeted
Manufacturers are increasingly vulnerable to cyber-attacks due to extensive supply chains and fragmented systems that leave gaps in security. With plenty of vulnerable endpoints, hackers can inject malware into their manufacturing targets through a weak-link partner or supplier. This explains how malware has outpaced social engineering attacks in the manufacturing vertical.
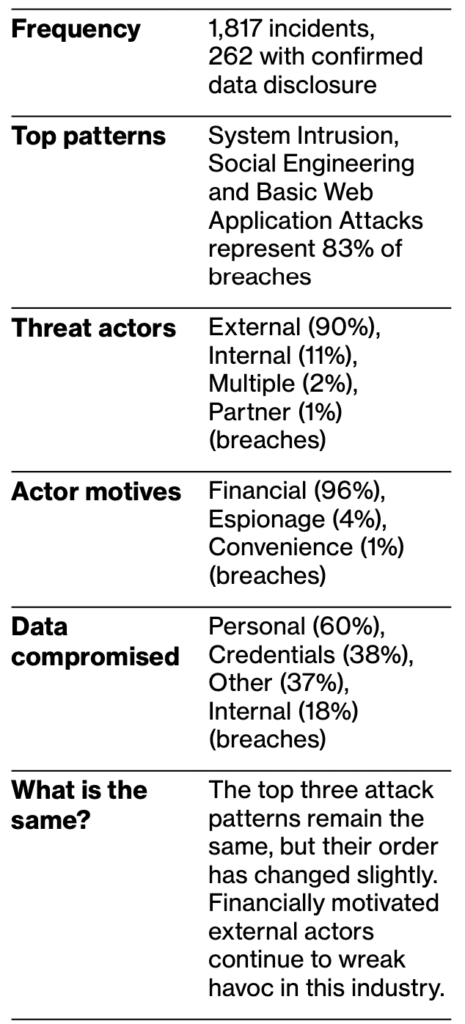
The same pattern can be seen in Oil/Gas & Utilities. The sheer number of electricity grids, power plants, and pipelines distributed across the country has rendered the Oil/Gas & Utilities sector an attractive target for cybercriminals. It’s not surprising that ransomware is responsible for approximately one out of three breaches in this vertical, with espionage playing a larger role in the threat actors’ motivations.
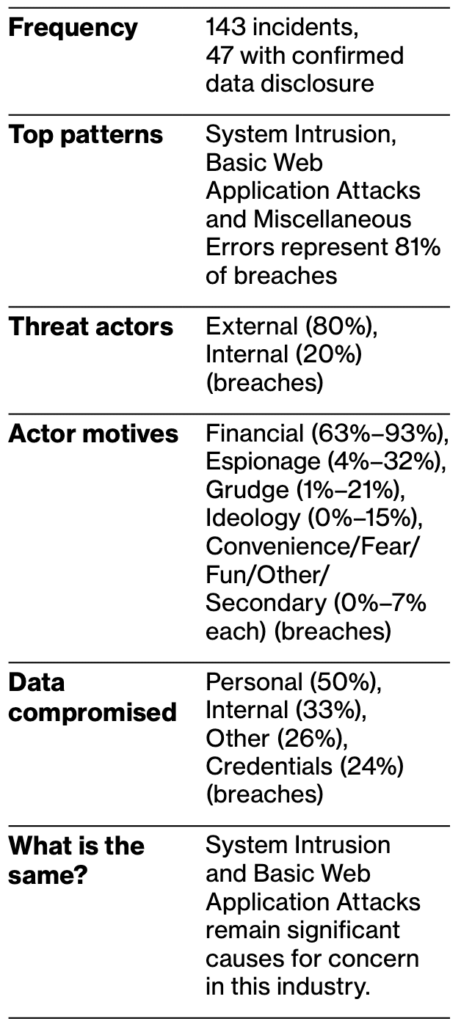
How Votiro can help: Considering the significant risk facing these verticals and the critical nature of the assets in these industries, Manufacturing (and Oil/Gas & Utilities) organizations should significantly value the advanced malware protection offered by Votiro.
Key Learning #9: SMEs are at risk
Small and medium-sized enterprises (SMEs) are experiencing breach incidents at a 50% higher rate than Enterprises. These businesses are particularly susceptible to cyber breaches due to several factors. While large organizations often have dedicated cybersecurity teams and resources, SMEs may have limited budgets and fewer personnel with specialized expertise to combat these threats.
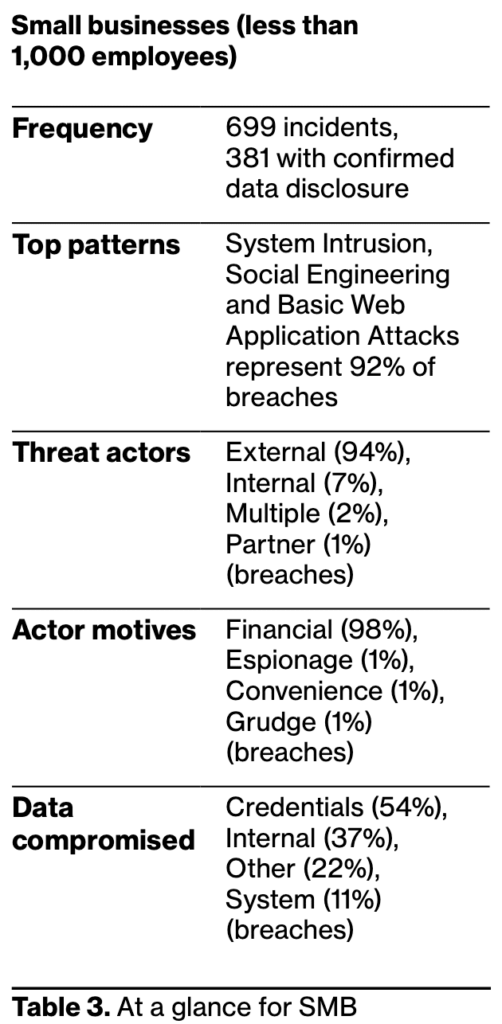
How Votiro can help: Instead of SMEs using detection techniques that require the ability to deploy a response, Votiro’s technology proactively disarms any and all files entering the organizations with no additional resources or effort required.
The Votiro Solution
The Verizon 2023 DBIR report underscores the importance of organizations reevaluating their cybersecurity strategies. It highlights the rapid changing of threats and the swift evolution of attack strategies. Enterprises should foster a cybersecurity culture that extends beyond IT departments, promoting vigilance, resilience, and continuous adaptation to emerging threats. Votiro delivers a comprehensive approach that provides protection where other security solutions and standard malware prevention methods fall short.
Contact us today to learn more about how Votiro leads the way in preventing hidden threats in files, and securing your organization while maintaining productivity. And if you’re ready to try Votiro for yourself, start today with a free 30-day trial.
News you can use
Stay up-to-date on the latest industry news and get all the insights you need to navigate the cybersecurity world like a pro. It's as easy as using that form to the right. No catch. Just click, fill, subscribe, and sit back as the information comes to you.
Sign-up Here!
Subscribe to our newsletter for real-time insights about the cybersecurity industry.



