Resource
Center
News You Can Use
Stay up-to-date on the latest industry news, plus get all the insights you need to navigate the cybersecurity world like a pro.
All Resources

Cloud Security in Two Parts: Masking and Sanitization

How to Stay GDPR-Compliant Without Blocking Business Productivity

The Hidden Risks in AI Training Data—And How to Eliminate Them

What is DSPM? Understanding Data Security Posture Management

What is Agentic AI? Plus, How to Secure It

The Votiro BrewFilter: Zero Trust Filtration for Your Next Mug

Zero Trust Data Detection & Response

Advanced Content Disarm & Reconstruction for Email

Menlo Secure Enterprise Browser and Votiro CDR

5 Must-Know Insights to Help Understand, and Prevent, Financial Cyber Attacks

Fragmented Solutions: The Hidden Cost of Security Silos

Beyond CASB: Strengthening Cloud Security with Deep File Inspection & Data Protection
AI Security in 2025: Why Data Protection Must Be Built In, Not Bolted On

Votiro’s Proven Protection: Retroscan for Zero-Day Threats

Proactive Data Security for Financial Services

Stopping CovertCatch – Securing Against Weaponized Job Offers

Menlo Security Acquires Votiro to Deliver Easy, AI-driven Data Security to Enterprises

Menlo Acquires Votiro to Deliver Workspace Security Solution

Stacking Up Data Security Solutions: DDR + DLP & DSPM
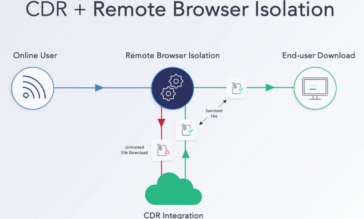
RBI Alone Isn’t Enough – How CDR Closes the File Security Gap
See Votiro DDR in Action
Book a live demo to see how Votiro Data Detection and Response can keep your organization safe and compliant with real-time data masking and proactive malware prevention.