Resource
Center
News You Can Use
Stay up-to-date on the latest industry news, plus get all the insights you need to navigate the cybersecurity world like a pro.
All Resources

The Cost of Data Privacy in 2024

Defending Data In Motion

Beyond the Breach: Lessons from the American Express Incident

Understanding CDR: The Backbone of Zero Trust Data Security

Broadcast Network Finds Multiple Solutions with Votiro

File Sanitization: Your Shield Against Malware

Votiro Listed in 2024 Partner Program Guide by CRN®
TAG Interview: Votiro Data Detection & Response with Eric Avigdor

Votiro Named 2x Silver Winner in 2024 Globee Cybersecurity Awards

Lessons from the UHC Change Healthcare Breach

Votiro & Owl Cyber Defense

The Secret to Optimizing Enterprise Data Detection & Response

Pi Day: How Hackers Slice Through Security Solutions

Microsoft Teams Technical Workshop & Demo

The Macros Playbook: Maximizing Benefits, Minimizing Risks

Security Priorities for Shipping and Logistics in 2024

What is Zero Trust: Ensuring Security in a Digital Age

A Deep Dive into the 2024 Prudential and LoanDepot Breaches

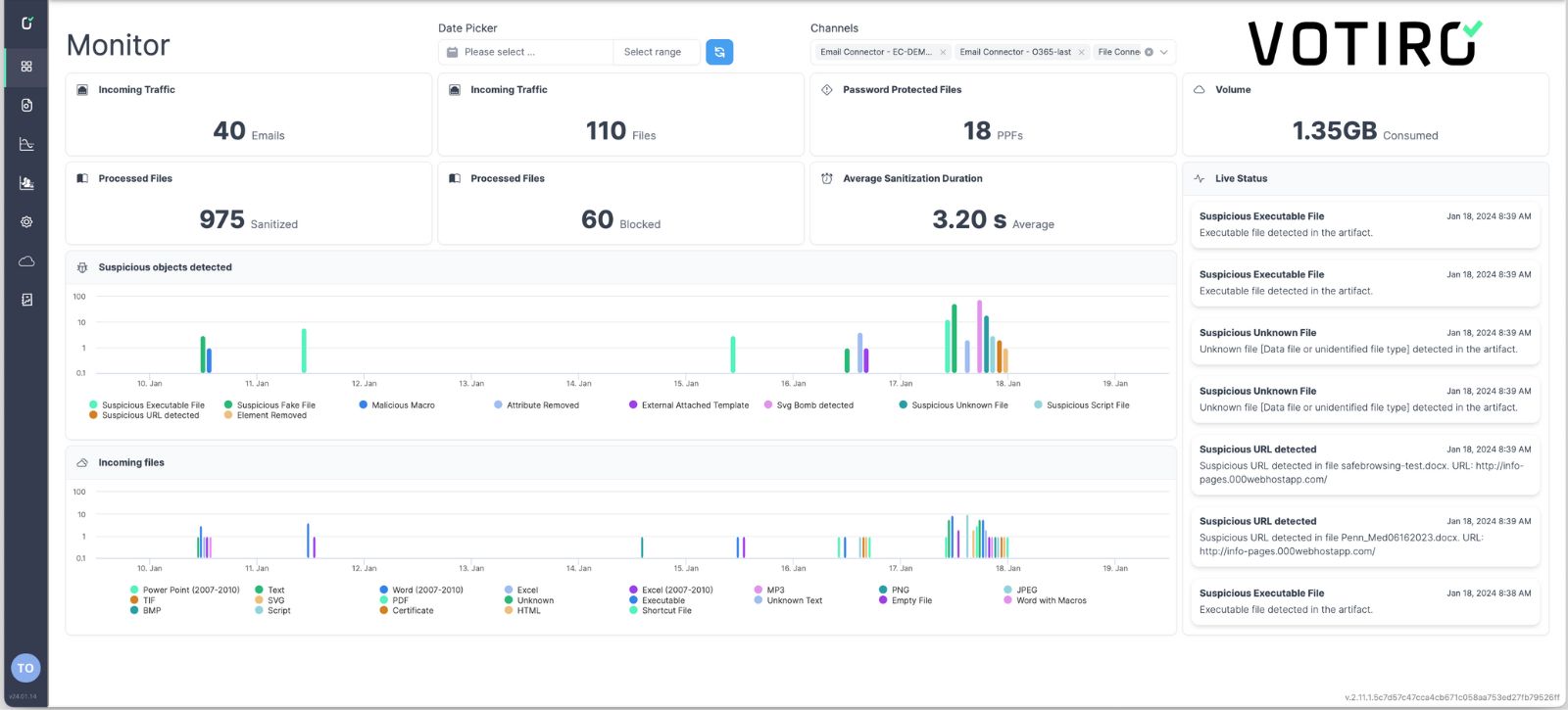
Votiro’s Platform Performance Metrics

Votiro’s Zero Trust Data Detection and Response
Get started for free.
Begin your free trial with Votiro to start
protecting your business from file-borne
threats, privacy risks, and more.