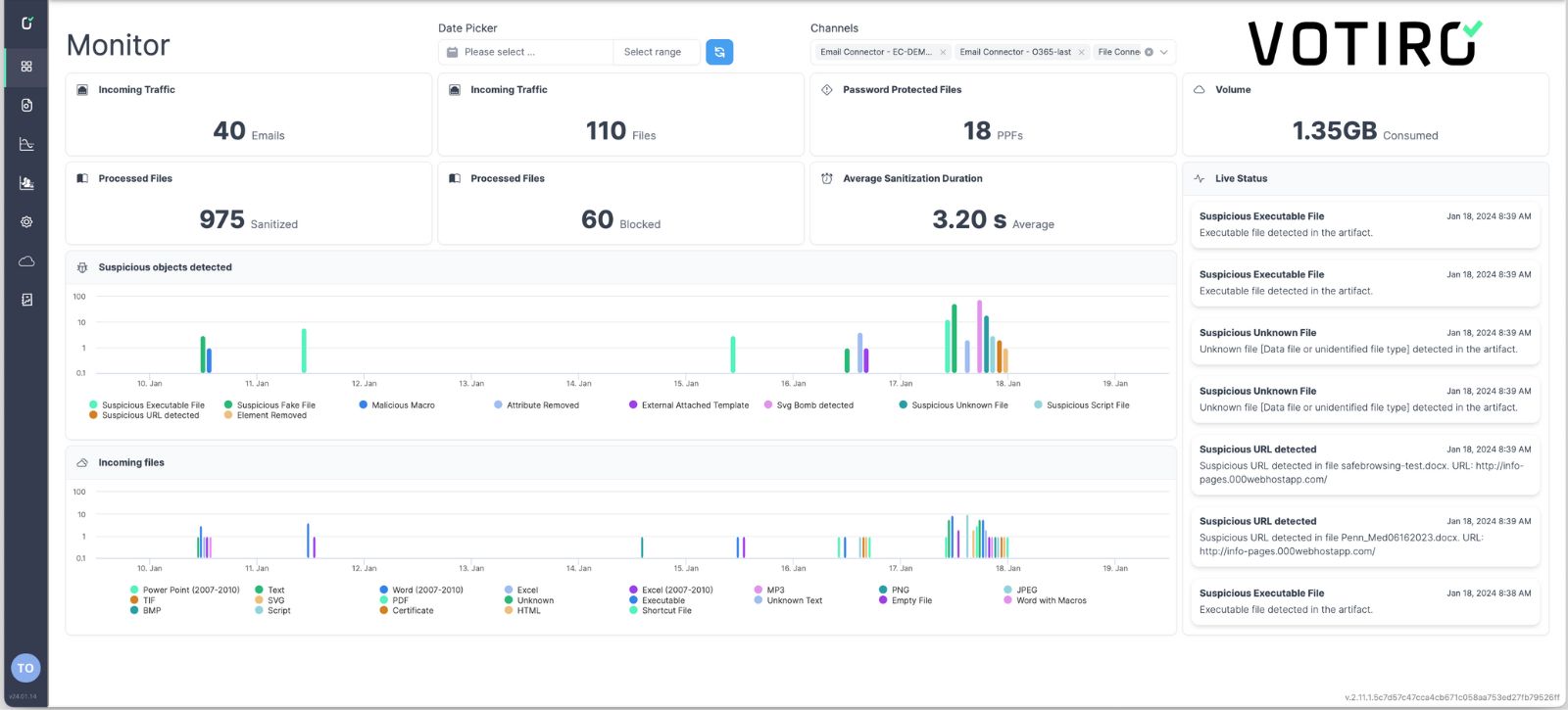
ProactiveReal-timeActionable We make file-borne threats and privacy risks a thing of the past.
Votiro is Zero Trust Content Security with Data Detection and Response in one platform. With proactive file-borne threat prevention, real-time privacy and compliance, and actionable data insights, our Zero Trust solution protects you from countless digital threats that pose unnecessary risks to your organization, your customers, and your reputation.
Explore our proven Data Security solutions.
Zero Trust threat prevention & data security is what we do.
Positive Selection®
is how we do it.
We take a Zero Trust approach to threat prevention and data exposure – one that removes all possible malware and privacy risks whether they’re known or not.
7+ Billion Files and  Breaches.
Breaches.
We Protect Leading Industries
Votiro enables organizations to digitize and collaborate without creating new operational burdens on IT teams or SOCs.












Join our growing list of
trusted Partners.
The Votiro Accelerate Program is designed to help Partners grow revenue by providing their customers with the best Zero Trust solution for threats and privacy the market has to offer.
A Mission Founded in Purpose
“As a pen tester, I sent compromised resumes to company HR departments. Every resume that went through was opened. Every single one. So, I decided there had to be a better solution to this common problem. And that solution is Votiro.”
Aviv Grafi | Votiro Founder & CTO
Get started for free.
Begin your free trial with Votiro to start
protecting your business from file-borne
threats, privacy risks, and more.